[sc name=”ad_1″] RMIScout performs wordlist and bruteforce attacks against exposed Java RMI interfaces to safely guess method signatures without...
Search Results For - Protection
[sc name=”ad_1″] Man-in-the-middle phishing attack using an Android app to grab session cookies for any website, which in turn allows to bypass 2...
[sc name=”ad_1″] UAC-A-Mola is a tool that allows security researchers to investigate new UAC bypasses, in addition to detecting and exploiting...
[sc name=”ad_1″] BOtB is a container analysis and exploitation tool designed to be used by pentesters and engineers while also being CI/CD friendly...
[sc name=”ad_1″] If for some reason your WordPress-based website has not yet been automatically updated to the latest version 5.1.1, it’s...
[sc name=”ad_1″] Cynet goes head-to-head with CrowdStrike, DarkTrace, Cylance, Carbon Black & Symantec, offering their unhappy customers a...
[sc name=”ad_1″] You must update your Google Chrome immediately to the latest version of the web browsing application. Security researcher Clement...
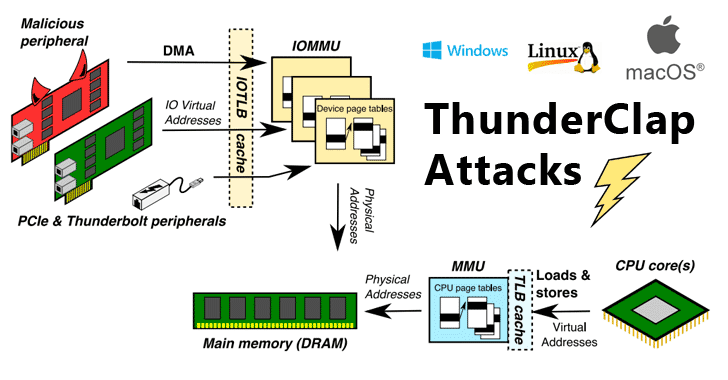
[sc name=”ad_1″] Security researchers have discovered a new class of security vulnerabilities that impacts all major operating systems, including...
[sc name=”ad_1″] Great news. If you have already installed the latest update of Google Play Services released earlier today, and your Android...
[sc name=”ad_1″] At NDSS Symposium 2019, a group of university researchers yesterday revealed newly discovered cellular network vulnerabilities...