DR.CHECKER: A Soundy Vulnerability Detection Tool for Linux Kernel Drivers Tested on Ubuntu >= 14.04.5 LTS 1. Setup The implementation is based on LLVM...
Search Results For - Processes
What this tool does is taking a file (any type of file), encrypt it, and embed it into an HTML file as ressource, along with an automatic download routine...
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...
Prochunter aims to find hidden process with all userspace and most of the kernelspace rootkits. This tool is composed of a kernel module that prints out all...
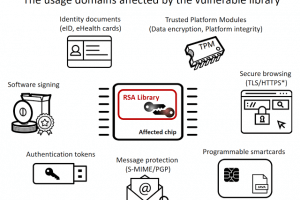
This tool is related to ACM CCS 2017 conference paper #124 Return of the Coppersmith’s Attack: Practical Factorization of Widely Used RSA Moduli. It enables...
The Firefox sandboxing innovation confines the browser from the operating system in a way to block web attacks from using a vulnerability in the browser engine...
The tool itself is impressive enough, serving as the backbone of the CIA’s malware processes, but there’s more. What’s interesting about the first leak in the...
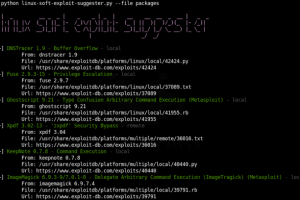
linux-soft-exploit-suggester finds exploits for all vulnerable software in a system helping with the privilege escalation. It focuses on software packages...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
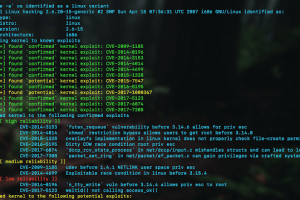
kernelpop is a framework for performing automated kernel exploit enumeration on Linux, Mac, and Windows hosts. Requirements python3 Currently supported...