[sc name=”ad_1″] CDK is an open-sourced container penetration toolkit, designed for offering stable exploitation in different slimmed containers...
Search Results For - Post Exploitation
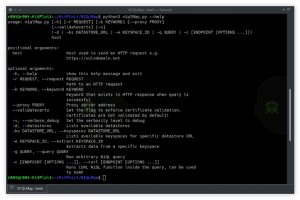
[sc name=”ad_1″] N1QLMap is an N1QL exploitation tool. Currently works with Couchbase database. The tool supports data extraction and performing...
[sc name=”ad_1″] The Nethive Project provides a Security Information and Event Management (SIEM) insfrastructure empowered by CVSS automatic...
[sc name=”ad_1″] h2cSmuggler smuggles HTTP traffic past insecure edge-server proxy_pass configurations by establishing HTTP/2 cleartext (h2c)...
[sc name=”ad_1″] Arcane is a simple script designed to backdoor iOS packages (iphone-arm) and create the necessar y resources for APT repositories...
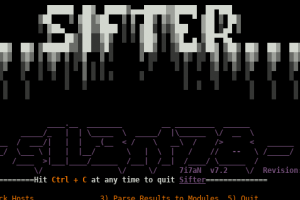
[sc name=”ad_1″] Sifter is a osint, recon & vulnerability scanner. It combines a plethara of tools within different module sets in order to...
[sc name=”ad_1″] AutoRDPwn is a post-exploitation framework created in Powershell, designed primarily to automate the Shadow attack on Microsoft...
[sc name=”ad_1″] A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting. Weapons Type Name Description Popularity...
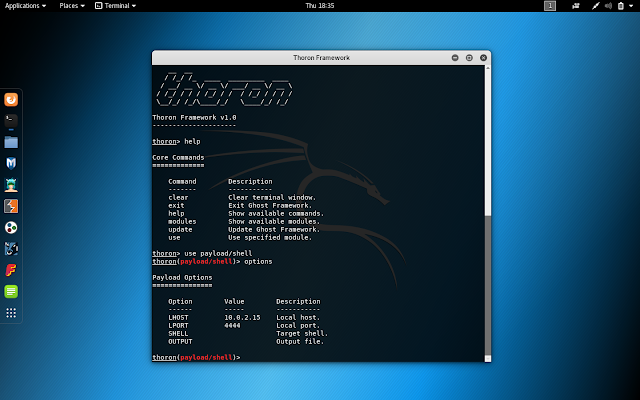
[sc name=”ad_1″] About Thoron Framework Thoron Framework is a Linux post-exploitation framework that exploit Linux tcp vulnerability to get shell...
[sc name=”ad_1″] FAT is a toolkit built in order to help security researchers analyze and identify vulnerabilities in IoT and embedded device...