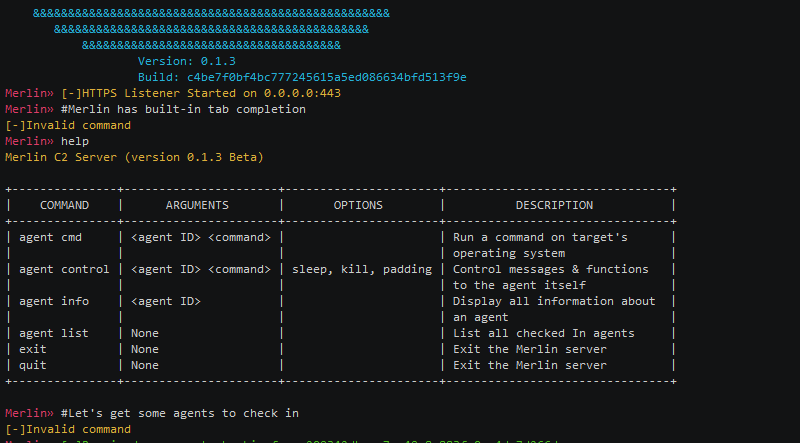
Merlin is a cross-platform post-exploitation framework that leverages HTTP/2 communications to evade inspection. HTTP/2 is a relatively new protocol that...
Search Results For - Post Exploitation
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...
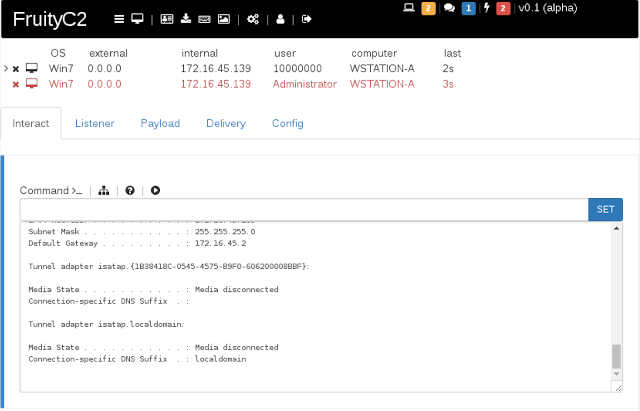
This is the initial release for FruityC2 (alpha version). Can be installed on any linux system, but the installation scripts are made for Debian based systems...
[sc name=”ad_1″] NERVE is a vulnerability scanner tailored to find low-hanging fruit level vulnerabilities, in specific application configurations...
[sc name=”ad_1″] BOtB is a container analysis and exploitation tool designed to be used by pentesters and engineers while also being CI/CD friendly...
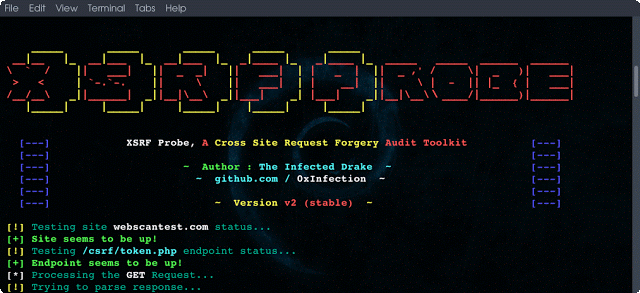
[sc name=”ad_1″] XSRFProbe is an advanced Cross Site Request Forgery (CSRF/XSRF) Audit and Exploitation Toolkit. Equipped with a Powerful Crawling...
XSStrike is an advanced XSS detection and exploitation suite. It has a powerful fuzzing engine and provides zero false positive result using fuzzy matching...
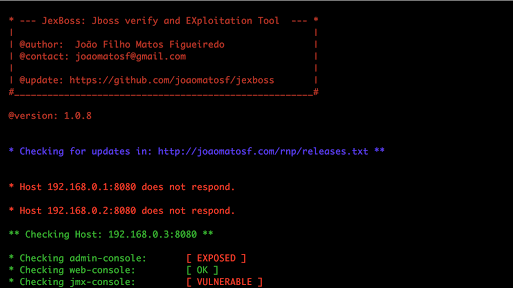
JexBoss is a tool for testing and exploiting vulnerabilities in JBoss Application Server and others Java Platforms, Frameworks, Applications, etc. Requirements...
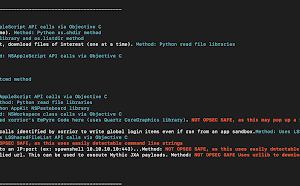
[sc name=”ad_1″] MacC2 is a macOS post exploitation tool written in python that uses Objective C calls or python libraries as opposed to command...
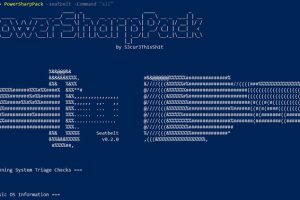
[sc name=”ad_1″] Many usefull offensive CSharp Projects wraped into Powershell for easy usage. Why? In my personal opinion offensive Powershell is...