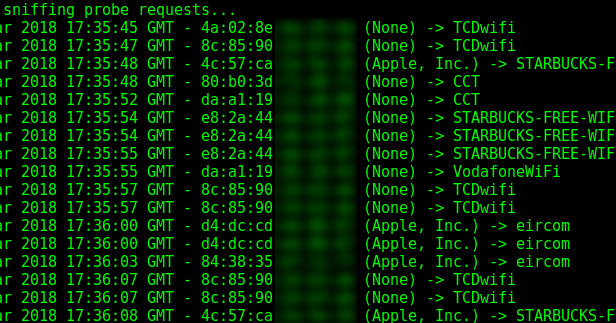
Toolkit allowing to sniff and display the Wi-Fi probe requests passing near your wireless interface. Probe requests are sent by a station to elicit information...
Search Results For - Phone
Author: David Hamilton The banking system is inefficient in its current state as it requires the use of multiple third-party verifications and transferring...
[sc name=”ad_1″] Hey Guys, In this video i show you how to Embed a Metasploit Payload in an Original .Apk File. Normally we have to install the...
This will be the beggining of a long series of the basics of linux, so let’s get started. What is Linux? Open-Source? What is the use of Linux? Linux is...
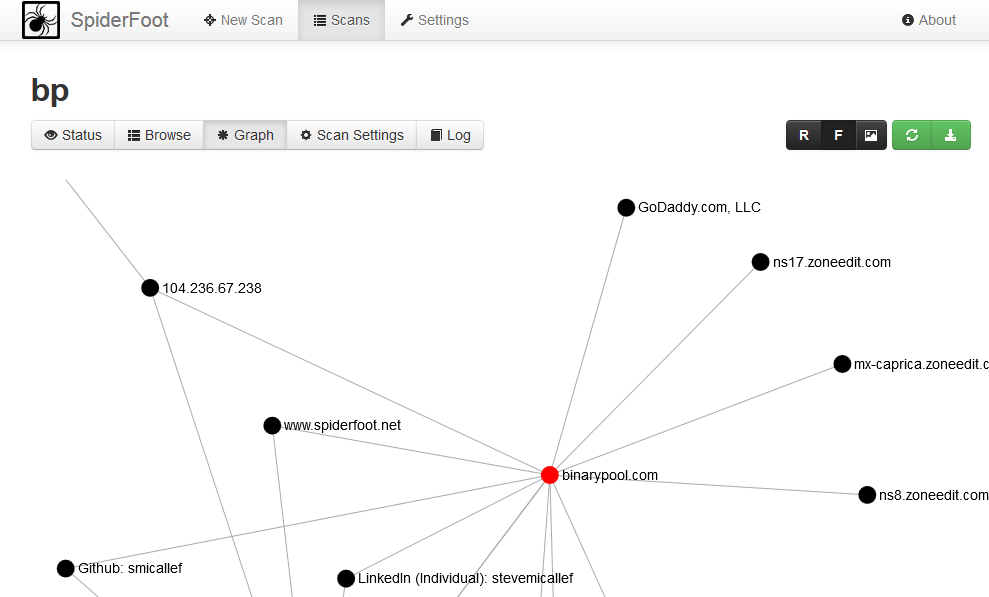
SpiderFoot is a reconnaissance tool that automatically queries over 100 public data sources (OSINT) to gather intelligence on IP addresses, domain names, e...
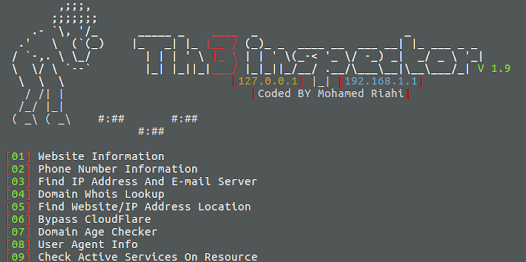
Tool For Information Gathering. Usage Short Form Long Form Description -i –info Website Information -n –number Phone Number Information -mx...
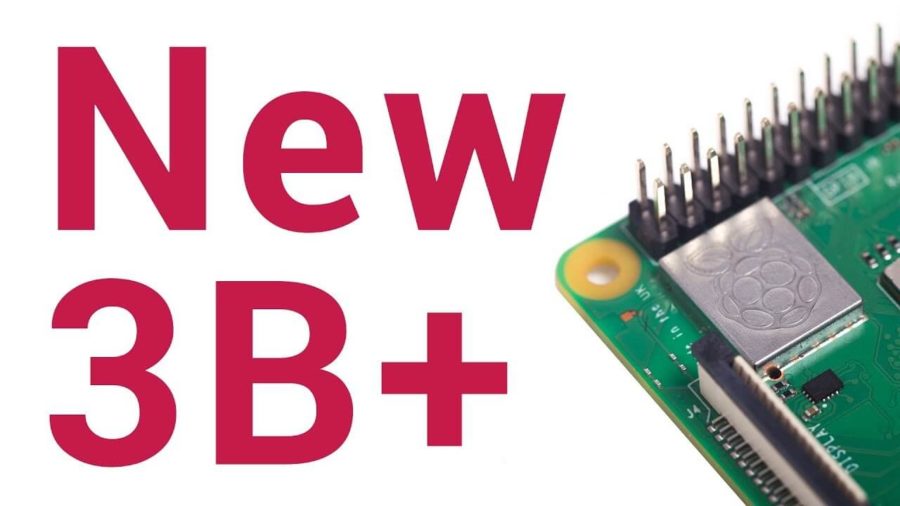
Raspberry Pi 3 Model B+ is now on sale for $35 (the same price as the existing Raspberry Pi 3 Model B), featuring: A 1.4GHz 64-bit quad-core ARM Cortex-A53 CPU...
Author: Erin Gorsline The move marks the first time a Japanese Bank will launch a cryptocurrency and exchange. Worth more than financial mega-giant Bank of...
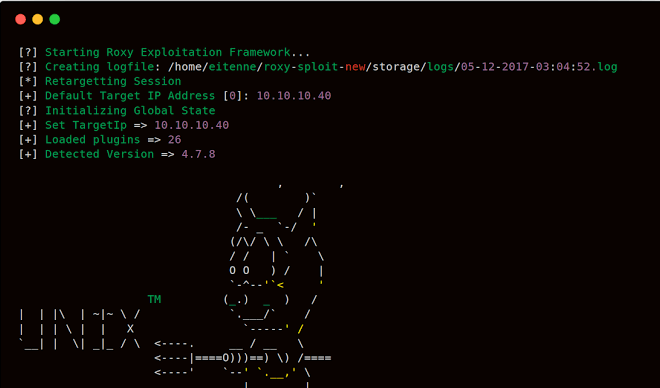
roxysploit is a community-supported, open-source and penetration testing suite that supports attacks for numerous scenarios. conducting attacks in the field...
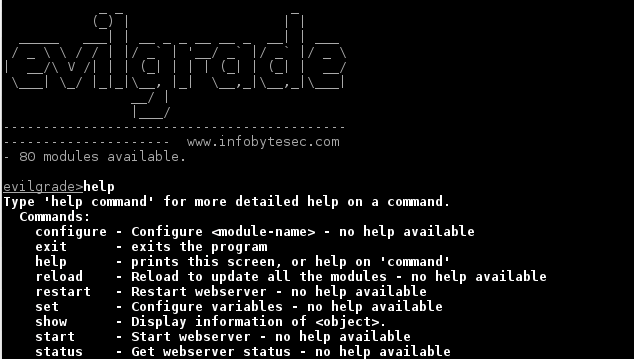
Evilgrade is a modular framework that allows the user to take advantage of poor upgrade implementations by injecting fake updates. It comes with pre-made...