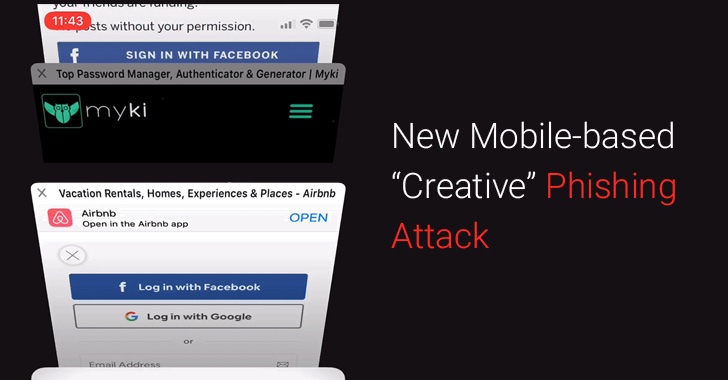
[sc name=”ad_1″] A cybersecurity researcher who last month warned of a creative phishing campaign has now shared details of a new but similar...
Search Results For - Phishing
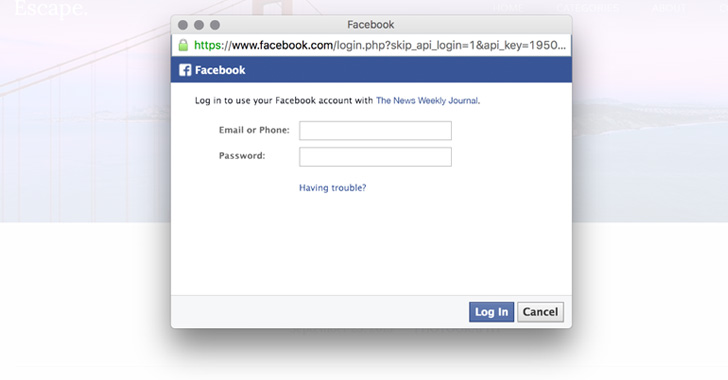
[sc name=”ad_1″] How do you check if a website asking for your credentials is fake or legit to log in? By checking if the URL is correct? By...
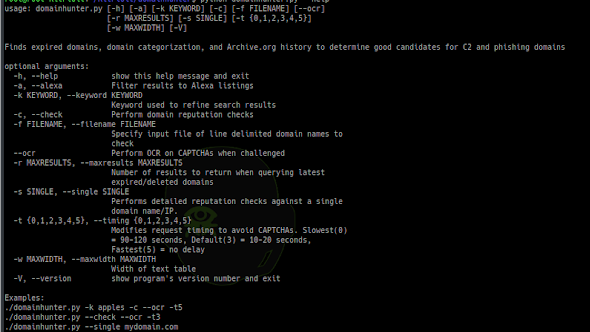
Domain name selection is an important aspect of preparation for penetration tests and especially Red Team engagements. Commonly, domains that were used...
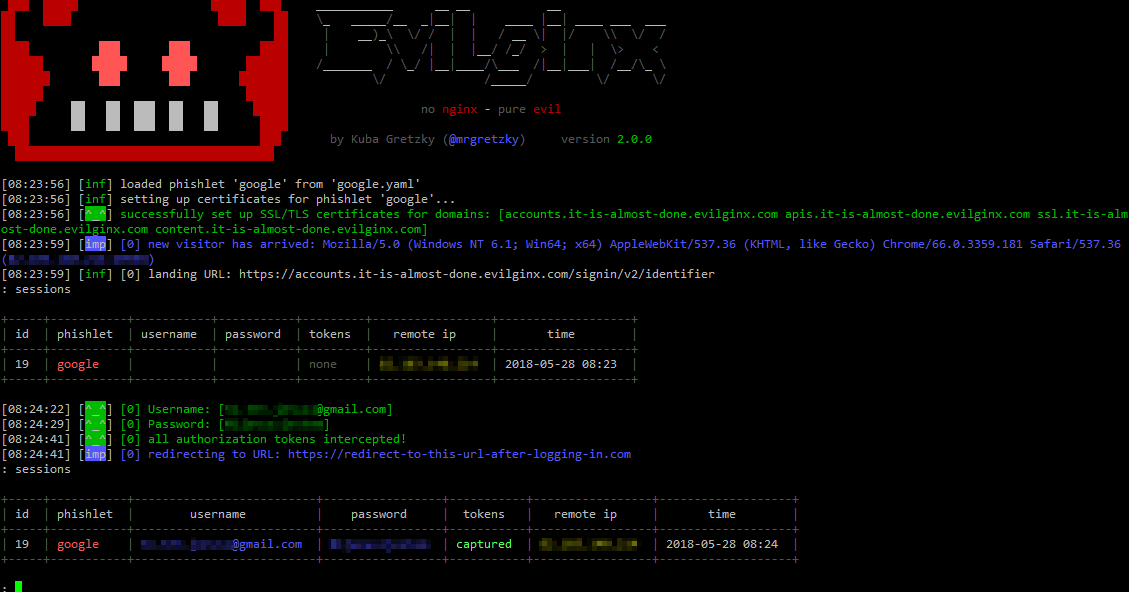
evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor...
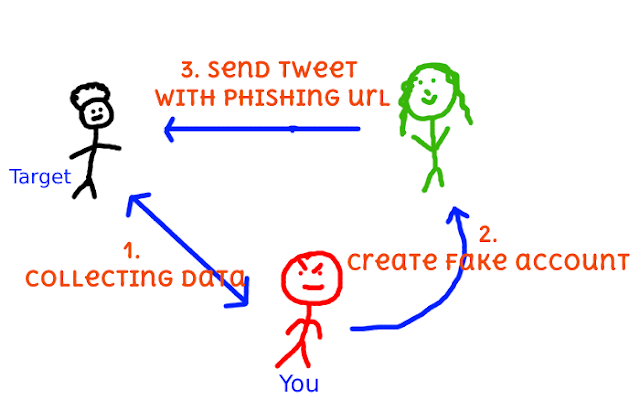
How it works? 1- Collect data from target’s twitter account 2- Find target’s friend and copy her/him account 3- Generate tweet automatically with...
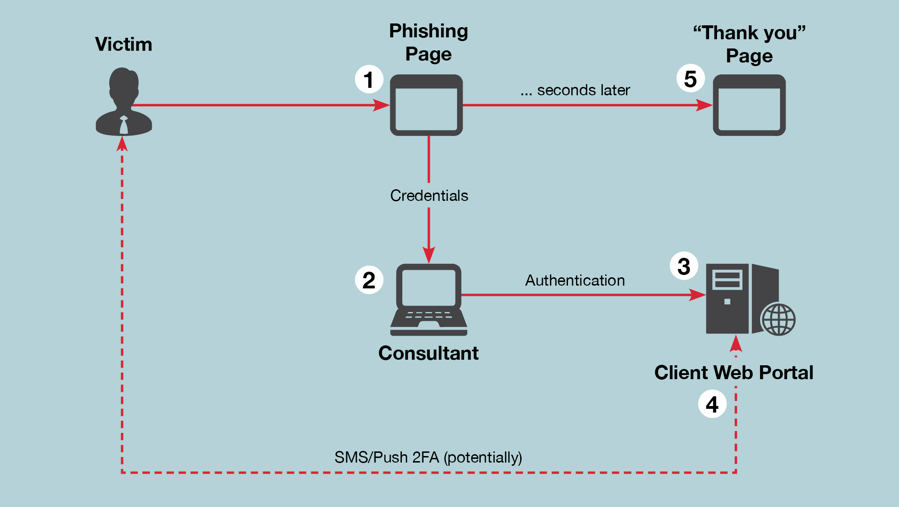
ReelPhish simplifies the real-time phishing technique. The primary component of the phishing tool is designed to be run on the attacker’s system. It consists...
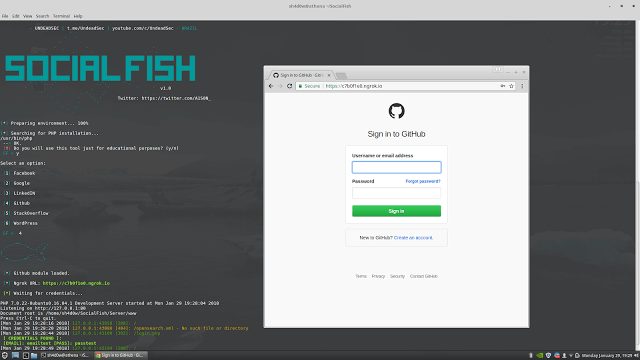
Ultimate phishing tool with Ngrok integrated. PREREQUISITES Python 2.7 Wget from Python PHP sudo TESTED ON Kali Linux – Rolling Edition Linux Mint...
Ultimate phishing tool with Ngrok integrated. PREREQUISITES Python 2.7 Wget from Python PHP TESTED ON Kali Linux – ROLLING EDITION CLONE git clone...
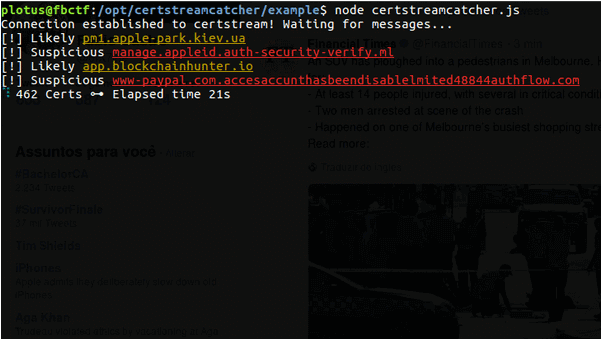
Catching phishing by observing certificate transparency logs. This tool is based on regex with effective standards for detecting phishing sites in real time...
Wifiphisher is a security tool that mounts automated victim-customized phishing attacks against WiFi clients in order to obtain credentials or infect the...