It seems sophisticated hackers have changed the way they conduct targeted cyber operations—instead of investing in zero-days and developing their malware; some...
Search Results For - Phishing Attacks
[sc name=”ad_1″] Great news. If you have already installed the latest update of Google Play Services released earlier today, and your Android...
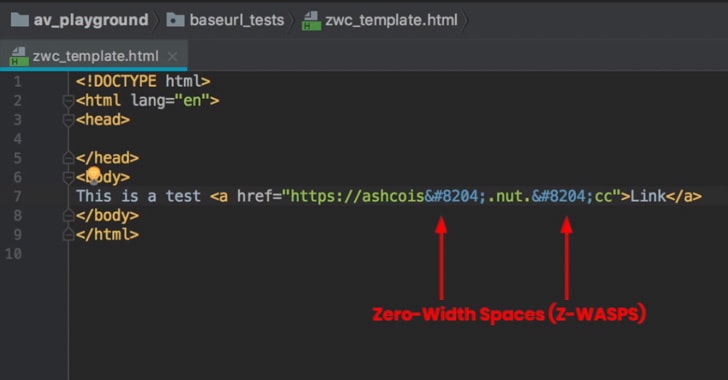
[sc name=”ad_1″] Security researchers have been warning about a simple technique that cybercriminals and email scammers are already being using in...
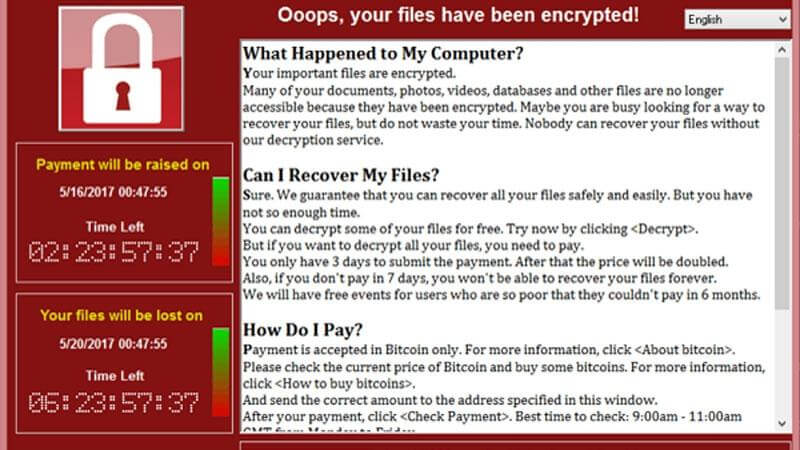
North Korea says there is no evidence to back the US claim it was behind the WannaCry ransomware attack. The US was “unreasonably accusing the DPRK...
Trape is a recognition tool that allows you to track people, the information you can get is very detailed. We want to teach the world through this, as large...
The Trump Organization dismissed the domain names were ever Hacked. But a review of internet credentials by the AP and cybersecurity specialists shows...
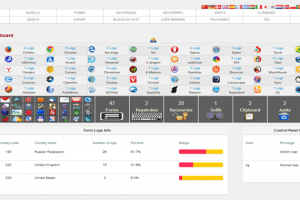
81 percent of data breaks last year involved weak, default or stolen passwords, and phishing attacks have advanced 65 percent year-on-year. Protecting online...
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
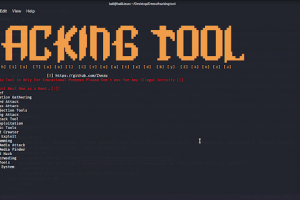
[sc name=”ad_1″] This project still in BETA so you may face problems, Please open an issue so i’ll fix them..!! Hackingtool Menu AnonSurf...
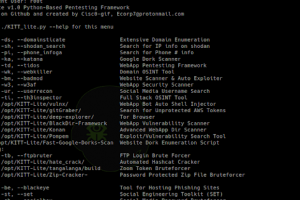
[sc name=”ad_1″] The KITT Penetration Testing Framework was developed as an open source solution for pentesters and programmers alike to compile...