[sc name=”ad_1″] Phishing Simulation mainly aims to increase phishing awareness by providing an intuitive tutorial and customized assessment...
Search Results For - Pentest
[sc name=”ad_1″] stegify is a simple command line tool capable of fully transparent hiding any file within an image. This technique is known as LSB...
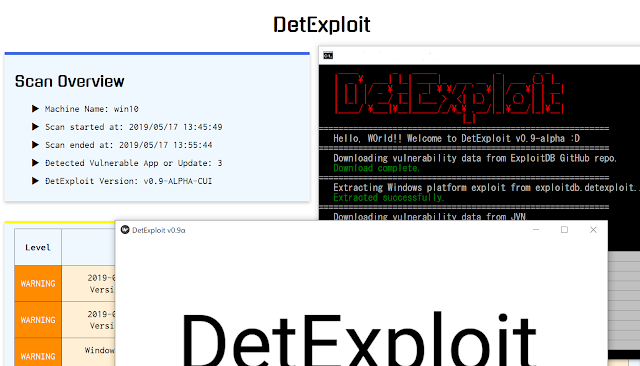
[sc name=”ad_1″] DetExploit is software that detect vulnerable applications and not-installed important OS updates on the system, and notify them...
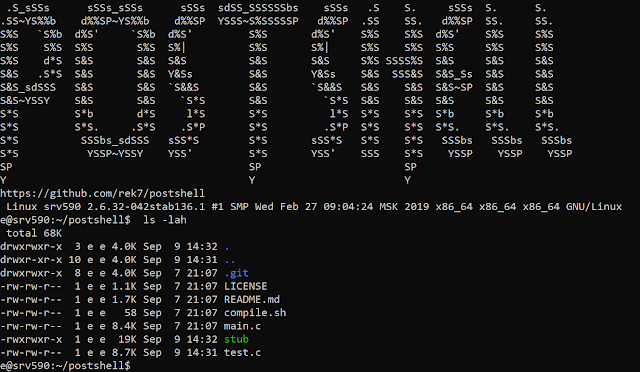
[sc name=”ad_1″] PostShell is a post-exploitation shell that includes both a bind and a back connect shell. It creates a fully interactive TTY...
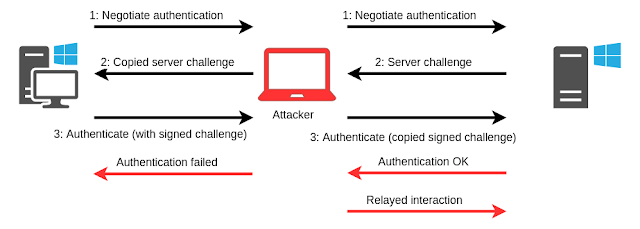
[sc name=”ad_1″] POC tools accompanying the blog Abusing Exchange: One API call away from Domain Admin. Requirements These tools require impacket...
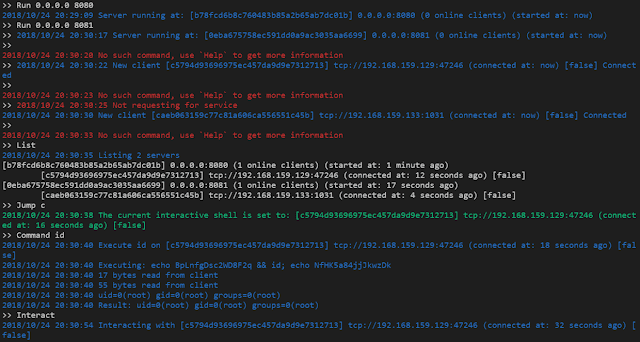
[sc name=”ad_1″] A modern multiple reverse shell sessions/clients manager via terminal written in go. Features Multiple service listening port...
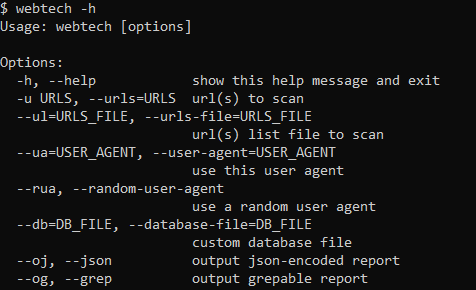
[sc name=”ad_1″] We knew that there are already tools doing this, for example Wappalyzer or CERN’s WAD, but we wanted a modular tool capable of...
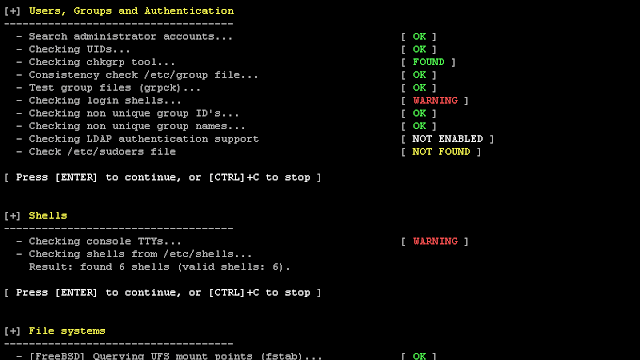
[sc name=”ad_1″] We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of...
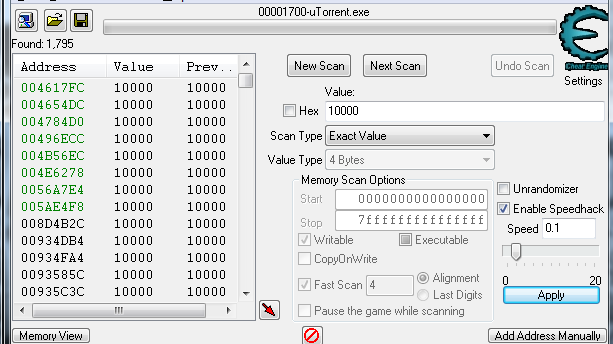
[sc name=”ad_1″] Cheat Engine is an open source tool designed to help you with modifying single player games running under window so you can make...
[sc name=”ad_1″] The Metasploit Project is a computer security project that provides information on vulnerabilities, helping in the development of...