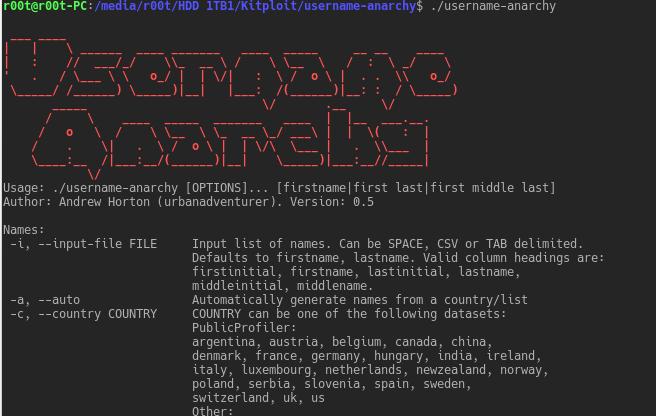
Tools for generating usernames when penetration testing. Usernames are half the password brute force problem. This is useful for user account/password brute...
Search Results For - Passwords
BruteSpray takes nmap GNMAP/XML output and automatically brute-forces services with default credentials using Medusa. BruteSpray can even find non-standard...
Windows 10 Facial Recognition System Is Hackable According to some experienced cyber security researchers, it was revealed that the facial recognition system...
ADRecon is a tool which extracts various artifacts (as highlighted below) out of an AD environment in a specially formatted Microsoft Excel report that...
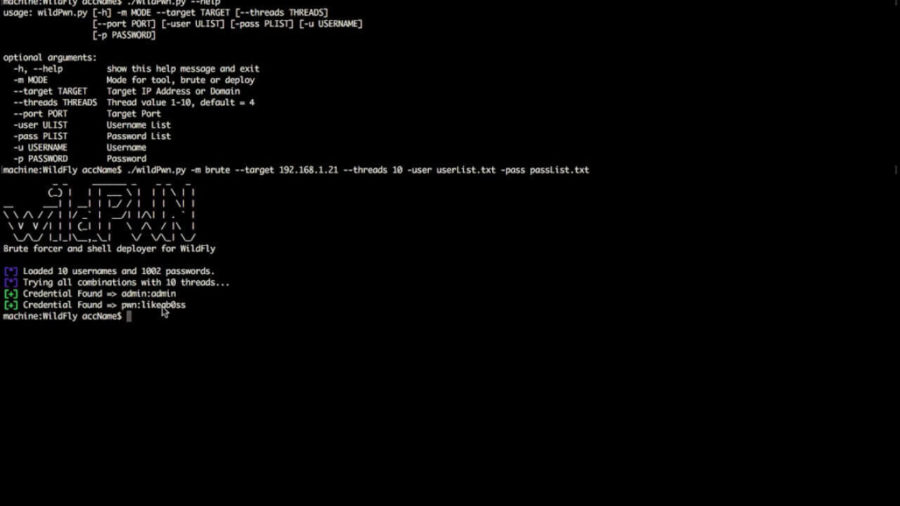
WildFly, formerly known as JBoss AS, or simply JBoss, is an application server authored by JBoss, now developed by Red Hat. WildFly is written in Java, and...
The U.S. federal officials have arrested two hackers who have pleaded guilty to computer-crimes charges for creating and distributing Mirai botnet that...
Bitcoin is breaking every record—after gaining 20% jump last week, Bitcoin price just crossed the $14,800 mark in less than 24 hours—and there can be no better...
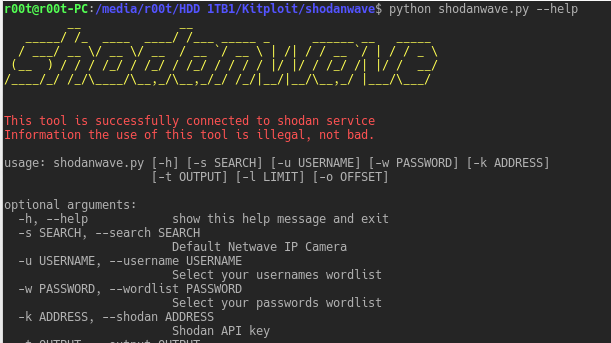
Shodanwave is a tool for exploring and obtaining information from cameras specifically Netwave IP Camera. The tool uses a search engine called shodan that...
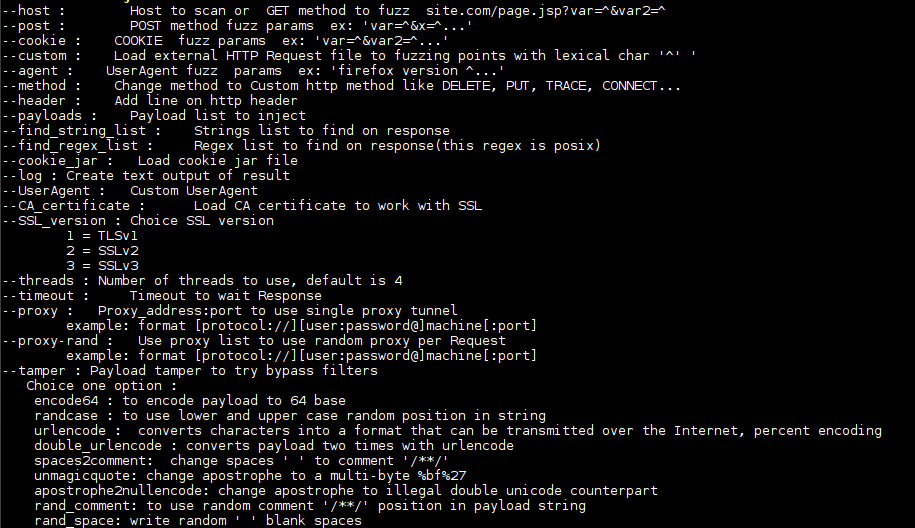
Web security tool to make fuzzing at HTTP inputs, made in C with libCurl. 0d1n is a tool for automating customized attacks against web applications. You can...
ratched is a Man-in-the-Middle (MitM) proxy that specifically intercepts TLS connections. It is intended to be used in conjunction with the Linux iptables...