[sc name=”ad_1″] A curated list of Android Security materials and resources For Pentesters and Bug Hunters. Blog AAPG – Android application...
Search Results For - OWASP Top 10
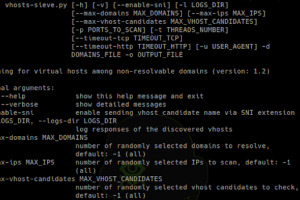
[sc name=”ad_1″] Searching for virtual hosts among non-resolvable domains. Installation git clone pip3 install -r vhosts-sieve/requirements.txt...
[sc name=”ad_1″] The script aims to help in classifying vulnerabilities in web applications. The methodology RecoX is arising can spot weaknesses...
[sc name=”ad_1″] A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting. Weapons Type Name Description Popularity...
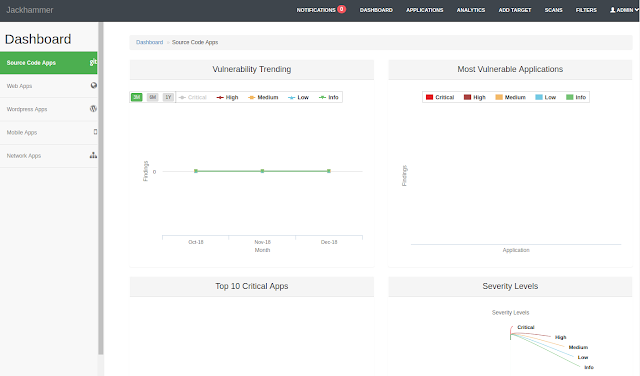
[sc name=”ad_1″] One Security vulnerability assessment/management tool to solve all the security team problems. What is Jackhammer? Jackhammer is a...
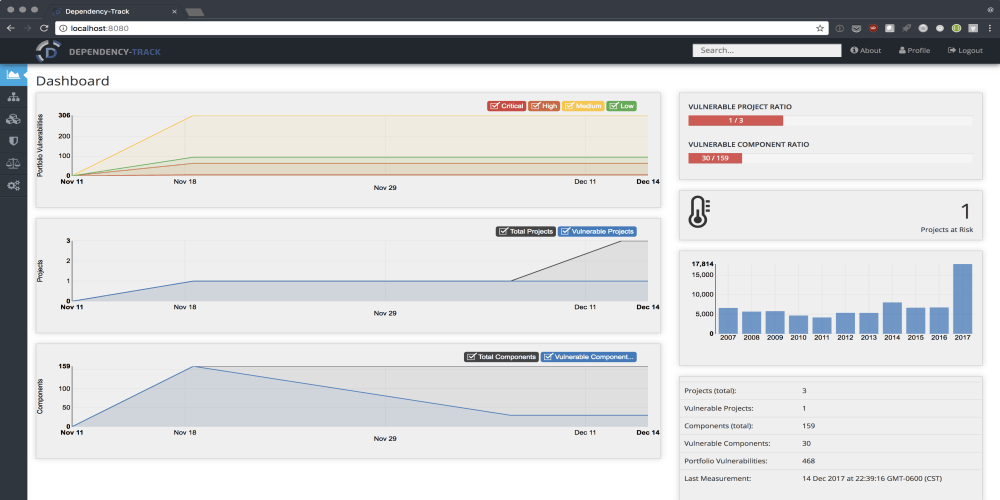
Modern applications leverage the availability of existing components for use as building blocks in application development. By using existing components...