[sc name=”ad_1″] Sharingan is a recon multitool for offensive security / bug bounty This is very much a work in progress and I’m relatively...
Search Results For - Nmap
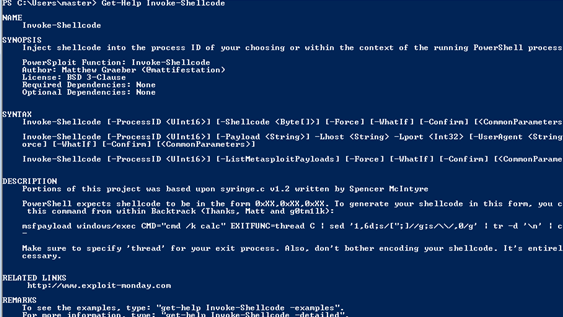
[sc name=”ad_1″] PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an...
[sc name=”ad_1″] Penta is is Pentest automation tool using Python3. (Future!) It provides advanced features such as metasploit and nexpose to...
[sc name=”ad_1″] Lockdoor Framework : A Penetration Testing Framework With Cyber Security Resources. 09/2019 : 1.0Beta Information Gathring Tools...
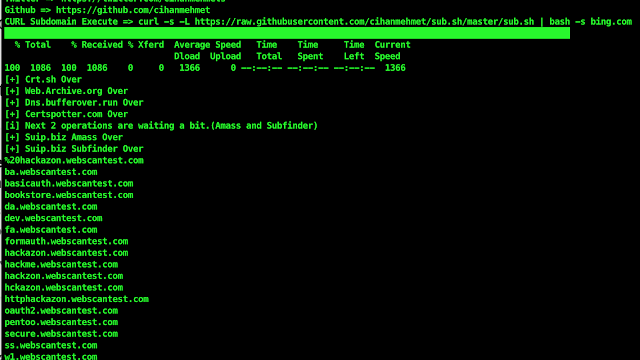
[sc name=”ad_1″] Online Subdomain Detect Script. USAGE Script bash sub.sh webscantest.com ./sub.sh webscantest.com Curl curl -s -L | bash -s...
[sc name=”ad_1″] FAT is a toolkit built in order to help security researchers analyze and identify vulnerabilities in IoT and embedded device...
[sc name=”ad_1″] Synopsis bscan is a command-line utility to perform active information gathering and service enumeration. At its core, bscan...
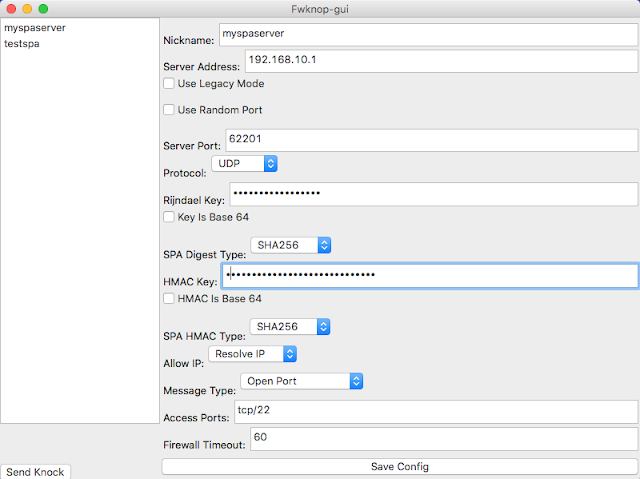
[sc name=”ad_1″] fwknop implements an authorization scheme known as Single Packet Authorization (SPA) for strong service concealment. SPA requires...
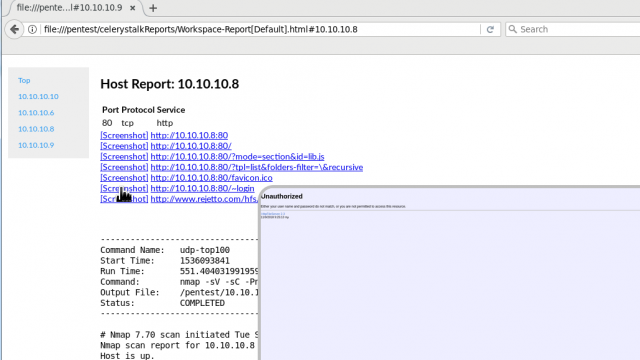
[sc name=”ad_1″] celerystalk helps you automate your network scanning/enumeration process with asynchronous jobs (aka tasks) while retaining full...
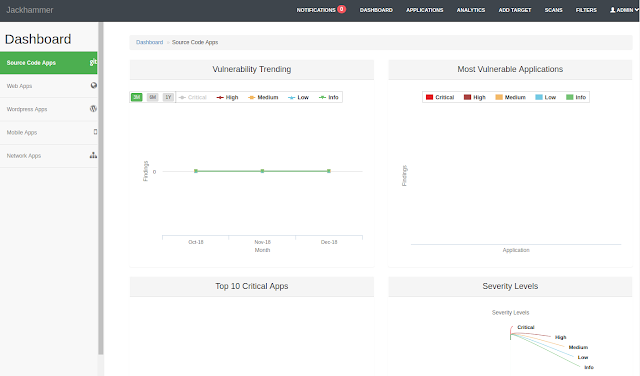
[sc name=”ad_1″] One Security vulnerability assessment/management tool to solve all the security team problems. What is Jackhammer? Jackhammer is a...