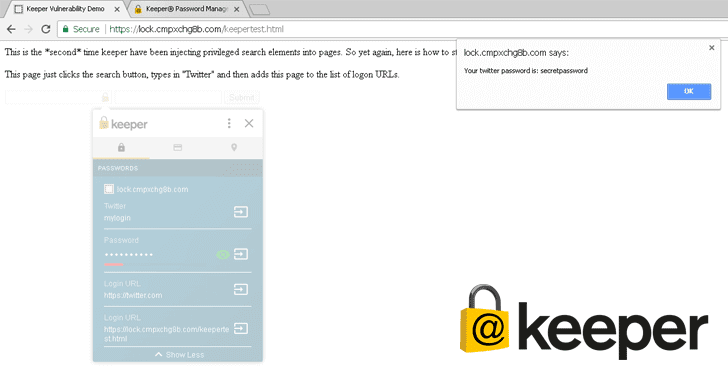
If you are running Windows 10 on your PC, then there are chances that your computer contains a pre-installed 3rd-party password manager app that lets attackers...
Search Results For - Microsoft
ADRecon is a tool which extracts various artifacts (as highlighted below) out of an AD environment in a specially formatted Microsoft Excel report that...
MoneyTaker hackers, A group of Russian hackers, has been laying waste to banks internationally and locally. In the past 18 months, this group has stolen a...
Search results will now show both multiple prospects and multiple sources, culled of a list of pre-approved data sources, to show Bing users various sides of...
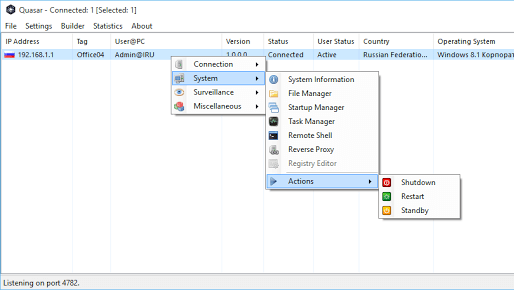
Quasar is a fast and light-weight remote administration tool coded in C#. Providing high stability and an easy-to-use user interface, Quasar is the perfect...
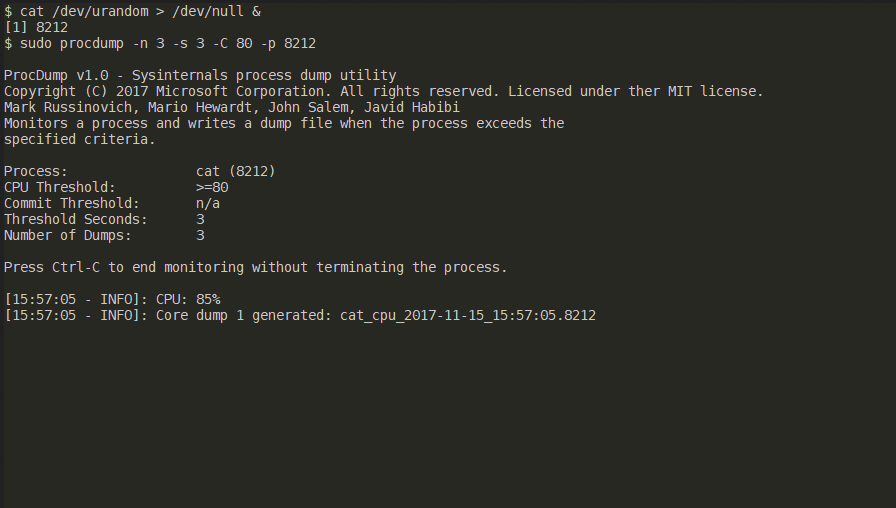
ProcDump is a Linux reimagining of the classic ProcDump tool from the Sysinternals suite of tools for Windows. ProcDump provides a convenient way for Linux...
Even software that has been built with secure development procedures may still be vulnerable to attack, due to flaws in the interpreted programming languages...
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...
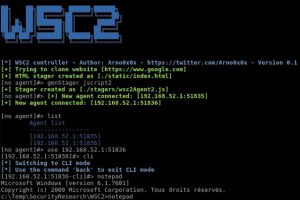
WSC2 is a PoC of using the WebSockets and a browser process to serve as a C2 communication channel between an agent, running on the target system, and a...
Security researchers have discovered a new, sophisticated form of malware based on the notorious Zeus banking Trojan that steals more than just bank account...