[sc name=”ad_1″] Google, the FBI, ad-fraud fighting company WhiteOps and a collection of cyber security companies worked together to shut down one...
Search Results For - Microsoft
[sc name=”ad_1″] Cybersecurity researchers have discovered a new zero-day vulnerability in Adobe Flash Player that hackers are actively exploiting...
AutoRDPwn is a script created in Powershell and designed to automate the Shadow attack on Microsoft Windows computers. This vulnerability allows a remote...
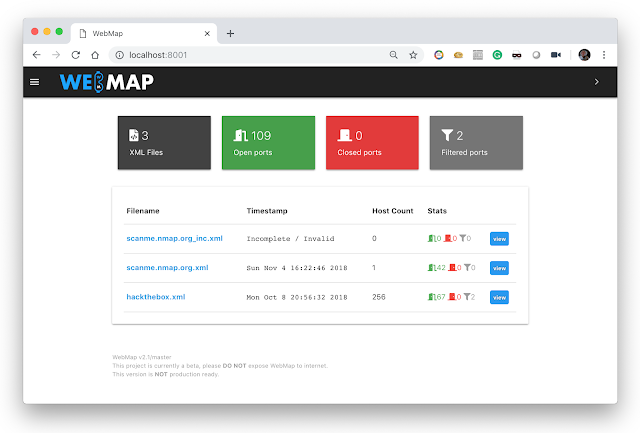
A Web Dashbord for Nmap XML Report Usage You should use this with docker, just by sending this command: $ mkdir /tmp/webmap $ docker run -d --name webmap -h...
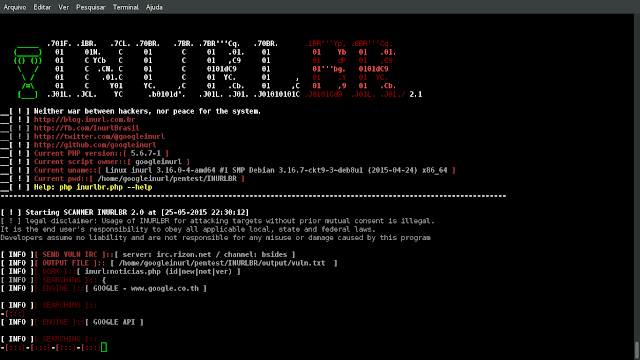
Advanced search in search engines, enables analysis provided to exploit GET / POST capturing emails & urls, with an internal custom validation junction for...
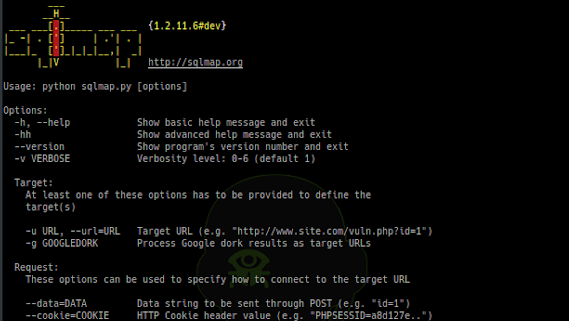
SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database...
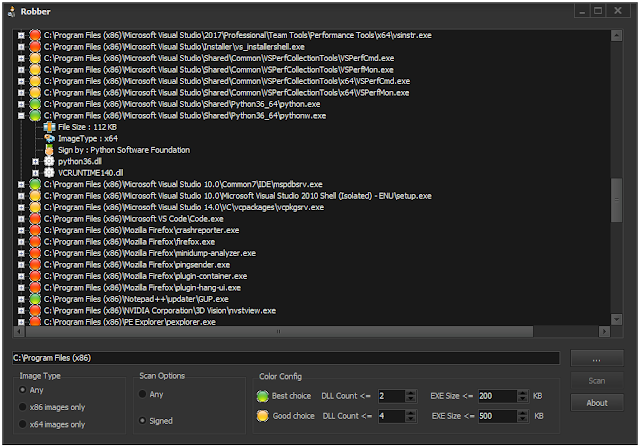
Robber is a free open source tool developed using Delphi XE2 without any 3rd party dependencies. What is DLL hijacking ?! Windows has a search path for DLLs in...
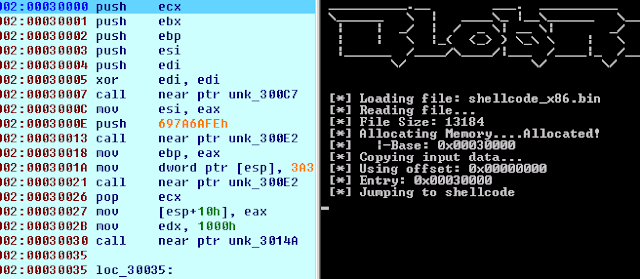
BlobRunner is a simple tool to quickly debug shellcode extracted during malware analysis. BlobRunner allocates memory for the target file and jumps to the base...
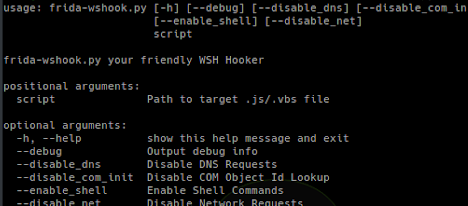
frida-wshook is an analysis and instrumentation tool which uses frida.re to hook common functions often used by malicious script files which are run using...
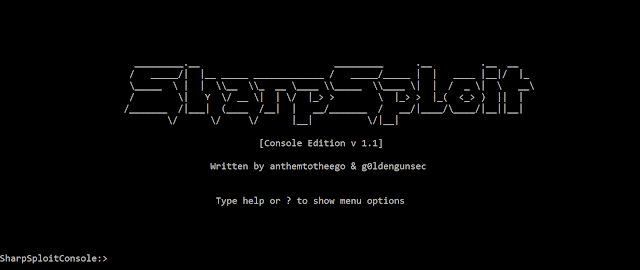
Console Application designed to interact with SharpSploit released by @cobbr_io SharpSploit is a tool written by @cobbr_io that combines many techniques/C#...