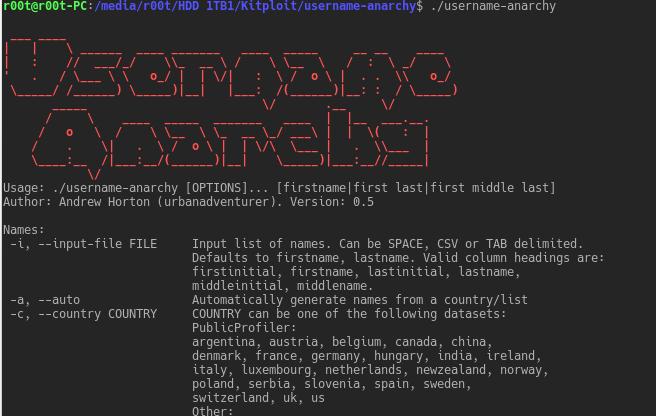
Tools for generating usernames when penetration testing. Usernames are half the password brute force problem. This is useful for user account/password brute...
Search Results For - Metadata
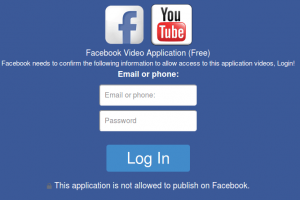
A new Facebook spam campaign has been detected by F-Secure security researchers, the campaign attracting users to phishing pages that attempt to fool users...
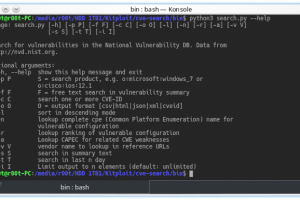
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
Multi-platform transparent client-side encryption of your files in the cloud. Cryptomator provides transparent, client-side encryption for your cloud. Protect...
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
Reverse Engineer .NET Assemblies dnSpy is a tool to reverse engineer .NET assemblies. It includes a decompiler, a debugger and an assembly editor (and more)...
The project is designed as a file resource cloner. Metadata, including digital signature, is extracted from one file and injected into another. Note: The...
Belati is tool for Collecting Public Data & Public Document from Website and other service for OSINT purpose. This tools is inspired by Foca and Datasploit...
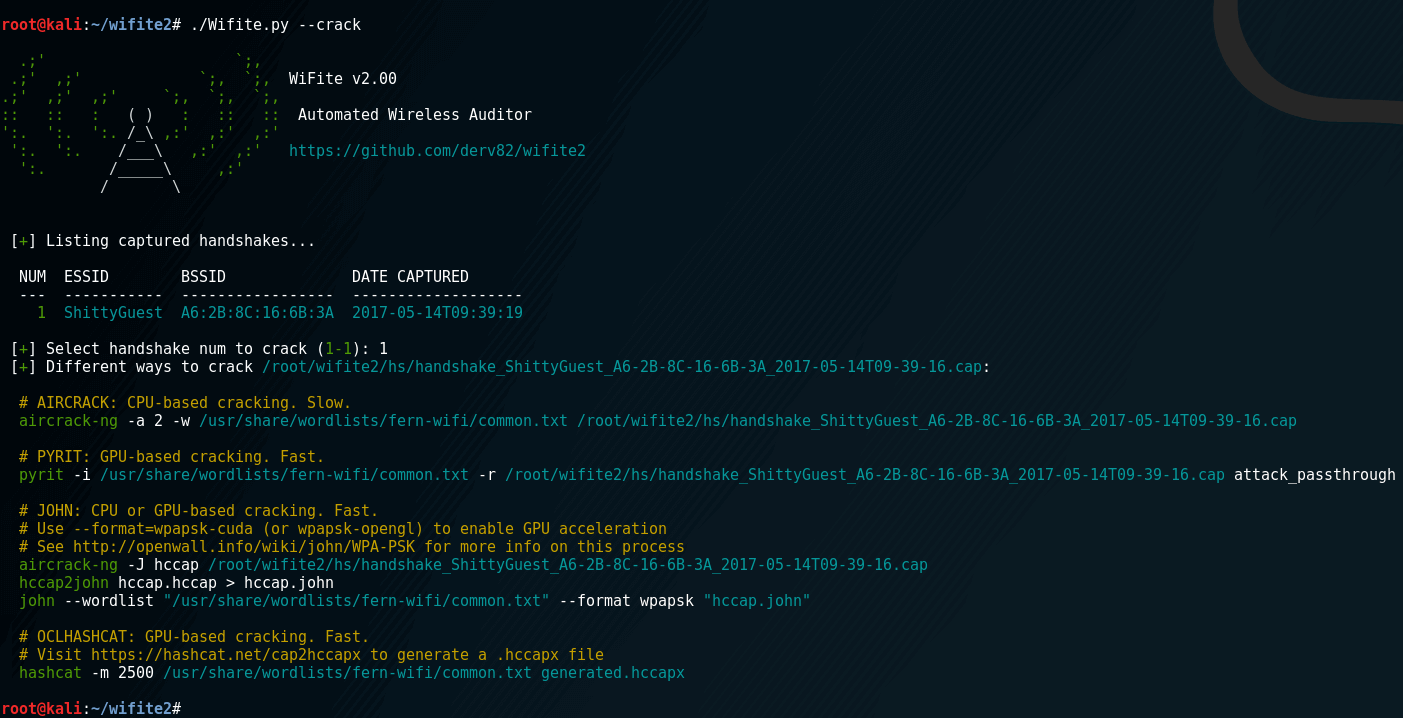
complete re-write of wifite, a Python script for auditing wireless networks. What’s new? Lots of files instead of “one big script”. Cleaner...
Sniffer is a C program that parses and interprets captured Ethernet traffic containing IP datagrams (UDP/TCP), and stores the captured payloads, email messages...