[sc name=”ad_1″] As indicated by sources like vulndb & cve, on a daily basis, approximately 50 new vulnerabilities become known to industry and...
Search Results For - Management
[sc name=”ad_1″] A set of scripts to help perform an online dictionary attack against a WPA3 access point. Wacker leverages the wpa_supplicant...
[sc name=”ad_1″] DNX Firewall is an optimized/high performance collection of applications or services to convert a standard linux system into a...
[sc name=”ad_1″] For the most up-to-date information on Anchore Engine, Anchore CLI, and other Anchore software, please refer to the Anchore...
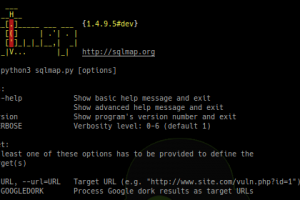
[sc name=”ad_1″] SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and...
[sc name=”ad_1″] What is “Kill Chain”? From Wikipedia: The term kill chain was originally used as a military concept related to the structure of an...
[sc name=”ad_1″] A security framework for enterprises and Red Team personnel, supports CobaltStrike’s penetration testing of other...
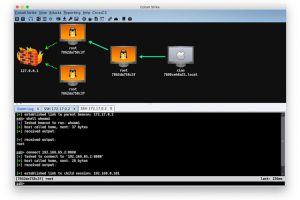
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...
[sc name=”ad_1″] ezEmu enables users to test adversary behaviors via various execution techniques. Sort of like an “offensive framework for...
[sc name=”ad_1″] Yeti is a platform meant to organize observables, indicators of compromise, TTPs, and knowledge on threats in a single, unified...