[sc name=”ad_1″] Features: Hacker Dashboard Hacker News [thehackernews.com/] New Exploits [Exploit-db.com] Hacking Tutorials Video [youtube.com]...
Search Results For - Logs
[sc name=”ad_1″] Depix is a tool for recovering passwords from pixelized screenshots. This implementation works on pixelized images that were...
[sc name=”ad_1″] This is a proof of concept of how a ransomware works, and some techniques that we usually use to hijack our files. This project is...
[sc name=”ad_1″] Karkinos is a light-weight ‘Swiss Army Knife’ for penetration testing and/or hacking CTF’s. Currently, Karkinos...
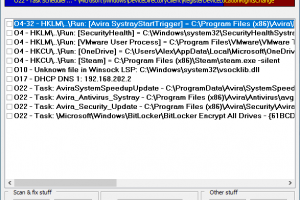
[sc name=”ad_1″] HiJackThis Fork is a free utility for Microsoft Windows that scans your computer for settings changed by adware, spyware, malware...
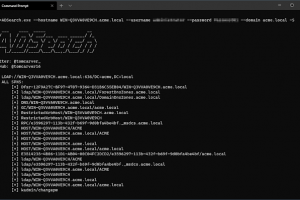
[sc name=”ad_1″] A tool written for cobalt-strike’s execute-assembly command that allows for more efficent querying of AD. Key Features List...
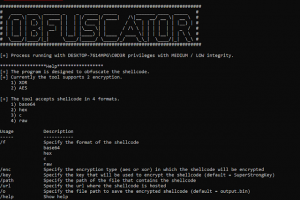
[sc name=”ad_1″] The program is designed to obfuscate the shellcode. Currently the tool supports 2 encryption. 1) XOR 2) AES The tool accepts...
[sc name=”ad_1″] Blog can be found at Script made for all your javascript recon automation in bugbounty. Just pass subdomain list to it and options...
[sc name=”ad_1″] enum4linux-ng.py is a rewrite of Mark Lowe’s (former Portcullis Labs now Cisco CX Security Labs) enum4linux.pl, a tool for...
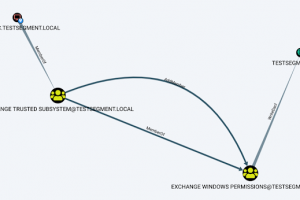
[sc name=”ad_1″] Aclpwn.py is a tool that interacts with BloodHound to identify and exploit ACL based privilege escalation paths. It takes a...