[sc name=”ad_1″] A Undetectable Payload Generation. This tool is for educational purpose only, usage of Kaiten for attacking targets without prior...
Search Results For - Logs
[sc name=”ad_1″] We are incredibly excited to announce the second release of 2020, Kali Linux 2020.2 A quick overview of what’s new since January:...
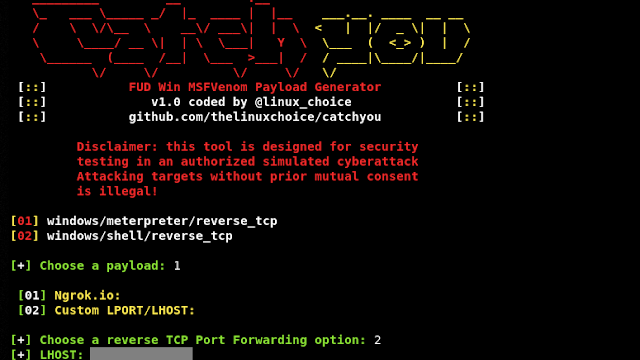
[sc name=”ad_1″] Fully Undetectable Win32 MSFVenom Payload Generator (meterpreter/shell reverse tcp) Author: github.com/thelinuxchoice/catchyou...
[sc name=”ad_1″] Shellerator is a simple command-line tool aimed to help pentesters quickly generate one-liner reverse/bind shells in multiple...
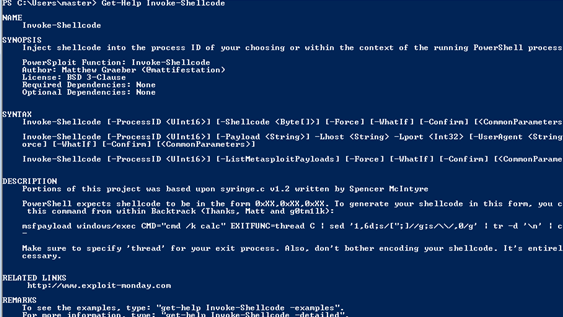
[sc name=”ad_1″] PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an...
[sc name=”ad_1″] Modern Denial-of-service ToolKit Main window Methods: Method Target Description SMS +PHONE SMS & CALL FLOOD NTP IP:PORT NTP...
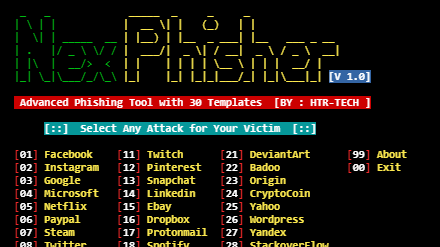
[sc name=”ad_1″] NexPhisher is an automated Phishing tool made for Termux & Linux .The phishing Pages are Taken from Zphisher under GNU General...
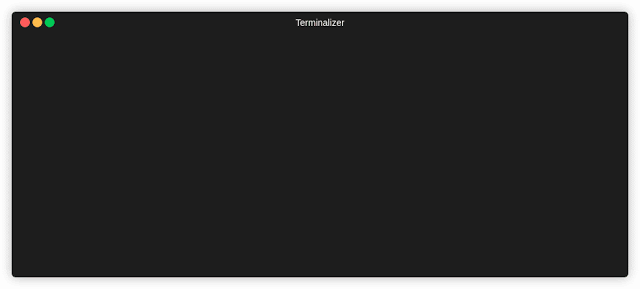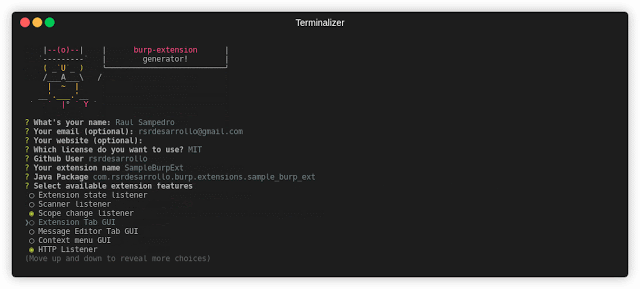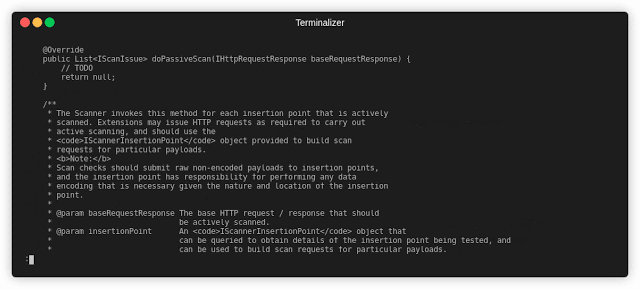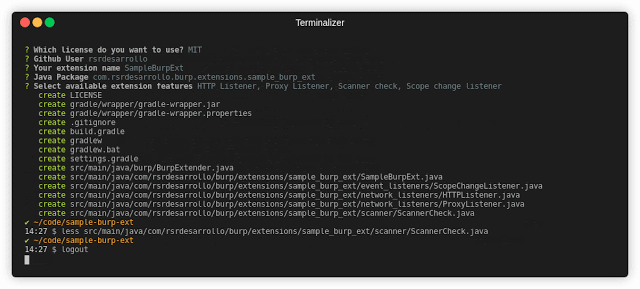
[sc name=”ad_1″] Everything You Need About Burp Extension Generation Installation First, install Yeoman and generator-burp-extension using npm (we...
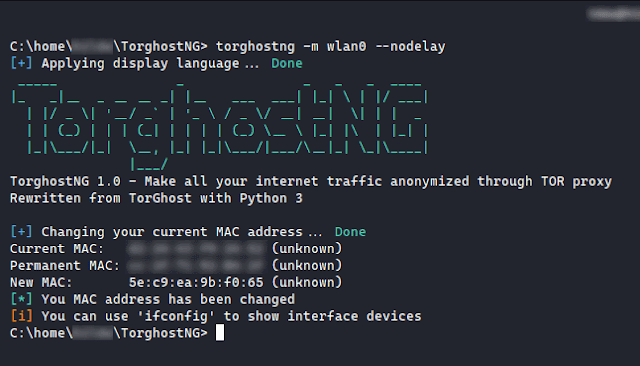
[sc name=”ad_1″] TorghostNG is a tool that make all your internet traffic anonymized through Tor network. Rewritten from TorGhost with Python 3...
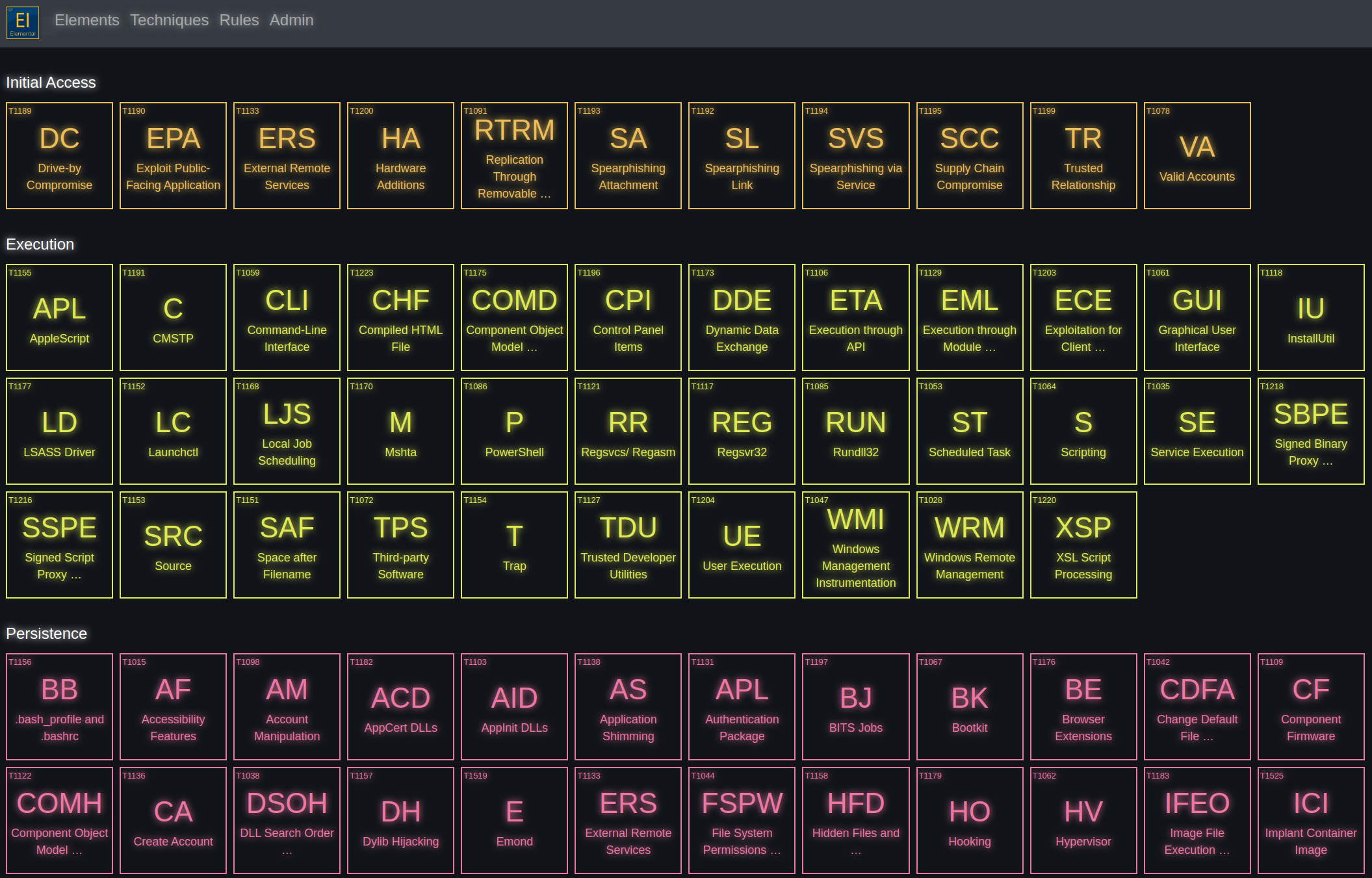
[sc name=”ad_1″] Elemental is a centralized threat library of MITRE ATT&CK techniques, Atomic Red Team tests, and over 280 Sigma rules. It...