[sc name=”ad_1″] SNIcat is a proof of concept tool that performs data exfiltration, utilizing a covert channel method via. Server Name Indication...
Search Results For - Linux
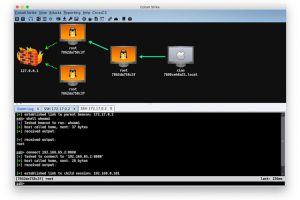
[sc name=”ad_1″] What is “Kill Chain”? From Wikipedia: The term kill chain was originally used as a military concept related to the structure of an...
[sc name=”ad_1″] A security framework for enterprises and Red Team personnel, supports CobaltStrike’s penetration testing of other...
[sc name=”ad_1″] iblessing iblessing is an iOS security exploiting toolkit, it mainly includes application information collection, static analysis...
[sc name=”ad_1″] Tested environments: Windows, MAC, linux, and windows subsystem for linux (WSL) What can SourceWolf do? Crawl through responses to...
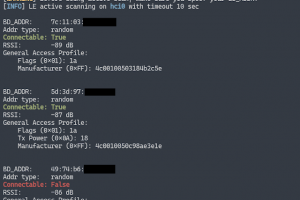
[sc name=”ad_1″] Bluescan is a open source project by Sourcell Xu from DBAPP Security HatLab. Anyone may redistribute copies of bluescan to anyone...
[sc name=”ad_1″] The all-in-one Red Team browser extension for Web Pentesters HackTools, is a web extension facilitating your web application...
[sc name=”ad_1″] ezEmu enables users to test adversary behaviors via various execution techniques. Sort of like an “offensive framework for...
[sc name=”ad_1″] This program allows the user to access a Memory Dump. It can also function as a plugin to the Volatility Framework (). This...
[sc name=”ad_1″] SecGen creates vulnerable virtual machines, lab environments, and hacking challenges, so students can learn security penetration...