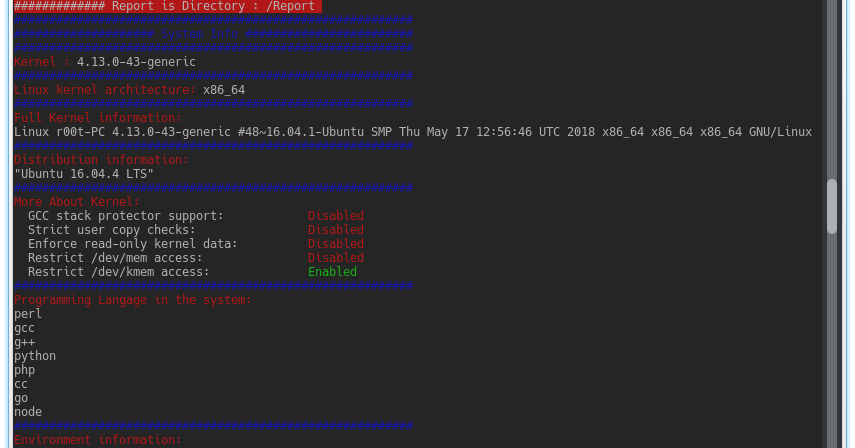
New Linux Privilege Escalation Tool. Getting Started System Information Gatherer Kernel Information Gatherer Checking Development environments on the system...
Search Results For - Linux Privilege Escalation
Often during the penetration test engagement the security analyst faces the problem of identifying privilege escalation attack vectors on tested Linux...
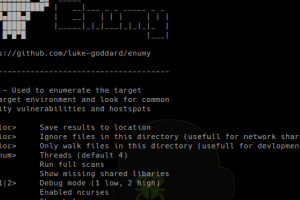
[sc name=”ad_1″] Enumy is portable executable that you drop on target Linux machine during a pentest or CTF in the post exploitation phase. Running...
[sc name=”ad_1″] Security researchers have discovered three vulnerabilities in Systemd, a popular init system and service manager for most Linux...
An Indian security researcher has discovered a highly critical flaw in X.Org Server package that impacts OpenBSD and most Linux distributions, including...
Security researchers have discovered a new privilege-escalation vulnerability in Linux kernel that could allow a local attacker to execute code on the affected...
[sc name=”ad_1″] Here you will find privilege escalation tools for Windows and Linux/Unix* (in some near future also for Mac). These tools search...
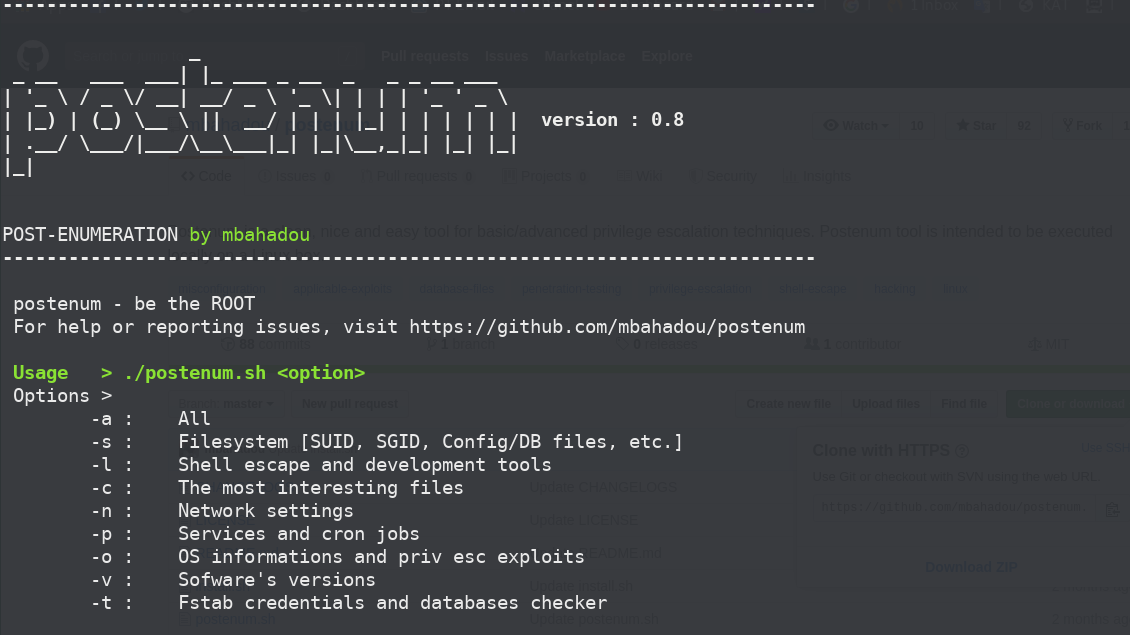
[sc name=”ad_1″] Postenum is a clean, nice and easy tool for basic/advanced privilege escalation vectors/techniques. Postenum tool is intended to...
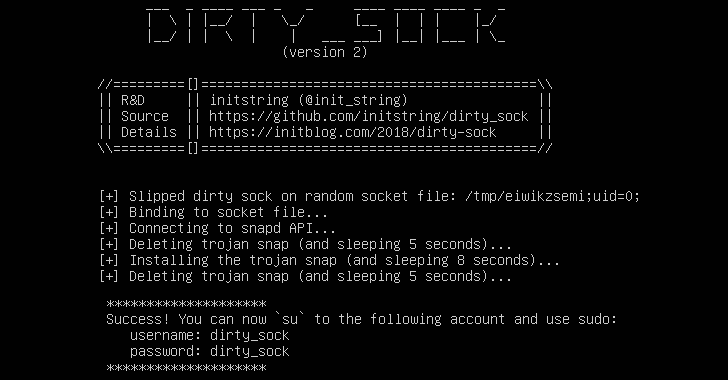
[sc name=”ad_1″] Ubuntu and some other Linux distributions suffer from a severe privilege escalation vulnerability that could allow a local...
Evil Remote Administration Tool (RAT) for macOS/OS X Features Emulate a terminal instance Simple extendable module system No bot dependencies (pure python)...