A series of recently disclosed critical Bluetooth flaws that affect billions of Android, iOS, Windows and Linux devices have now been discovered in millions of...
Search Results For - Kernel
Security GNU/Linux distribution designed with cloud pentesting and IoT security in mind. It includes a full portable laboratory for security and digital...
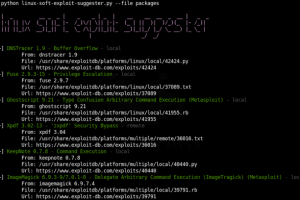
linux-soft-exploit-suggester finds exploits for all vulnerable software in a system helping with the privilege escalation. It focuses on software packages...
hashcat is the world’s fastest and most advanced password recovery utility, supporting five unique modes of attack for over 200 highly-optimized hashing...
Linux ELF x32 and x64 ASLR bypass exploit with stack-spraying. Properties: ASLR bypass Cross-platform Minimalistic Simplicity Unpatchable Dependencies: Linux 2...
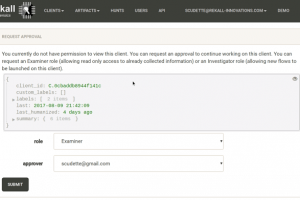
The Rekall Framework is a completely open collection of tools, implemented in Python under the Apache and GNU General Public License, for the extraction and...
Reptile is a LKM rootkit for evil purposes. If you are searching stuff only for study purposes, see the demonstration codes. Features Give root to unprivileged...
Bash script purposed for system enumeration, vulnerability identification and privilege escalation. MIDA Multitool draws functionality from several of my...
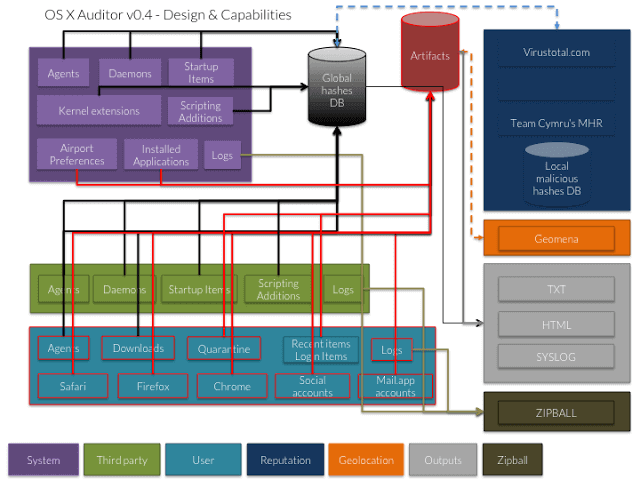
OS X Auditor is a free Mac OS X computer forensics tool. OS X Auditor parses and hashes the following artifacts on the running system or a copy of a system you...