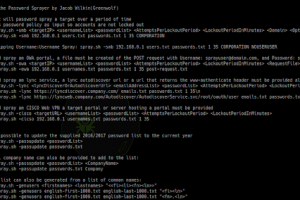
[sc name=”ad_1″] A Password Spraying tool for Active Directory Credentials by Jacob Wilkin(Greenwolf) Getting Started These instructions will show...
Search Results For - Kali Linux
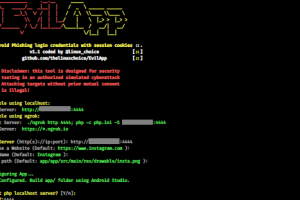
[sc name=”ad_1″] Man-in-the-middle phishing attack using an Android app to grab session cookies for any website, which in turn allows to bypass 2...
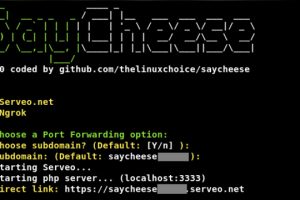
[sc name=”ad_1″] Take webcam shots from target just sending a malicious link. How it works? The tool generates a malicious HTTPS page using Serveo...
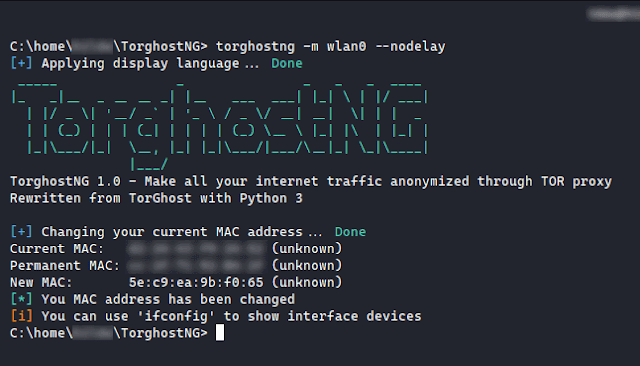
[sc name=”ad_1″] TorghostNG is a tool that make all your internet traffic anonymized through Tor network. Rewritten from TorGhost with Python 3...
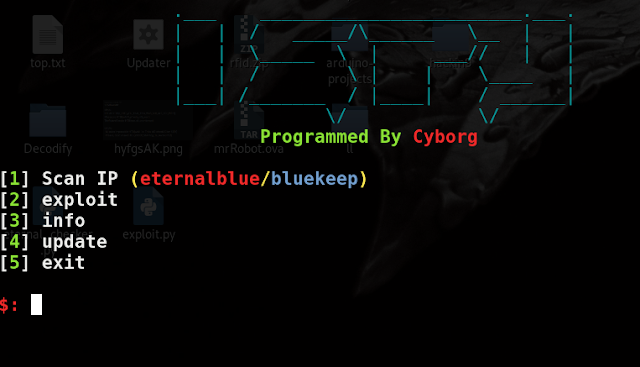
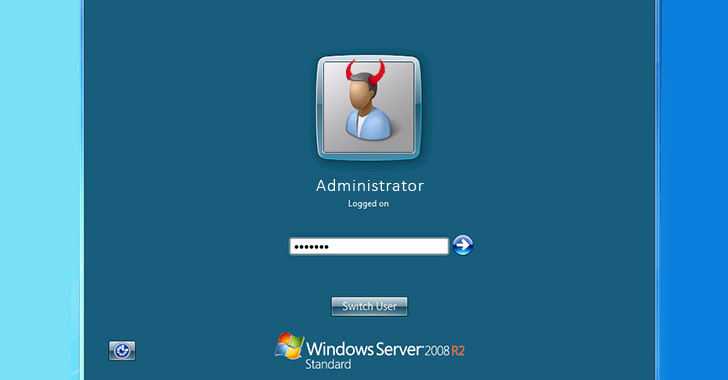
[sc name=”ad_1″] ispy : Eternalblue(ms17-010)/Bluekeep(CVE-2019-0708) Scanner and exploiter ( Metasploit automation ) How to install : git clone cd...
[sc name=”ad_1″] HRShell: An advanced HTTP(S) Reverse Shell built with Flask HRShell is an HTTPS/HTTP reverse shell built with flask. It’s...
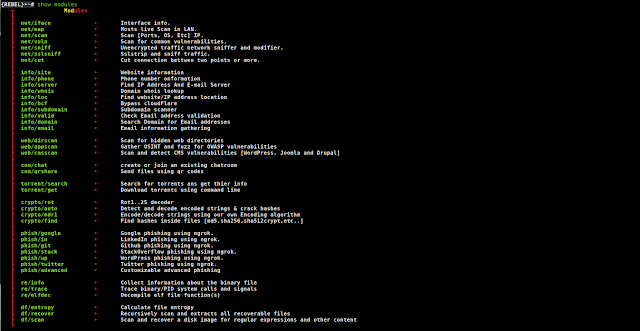
[sc name=”ad_1″] Rebel framework is an advanced and easy to use penetration testing framework.You can use it to automate the automation itself...
[sc name=”ad_1″] Synopsis bscan is a command-line utility to perform active information gathering and service enumeration. At its core, bscan...
[sc name=”ad_1″] You’ve always been warned not to share remote access to your computer with any untrusted people for many reasons—it’s...
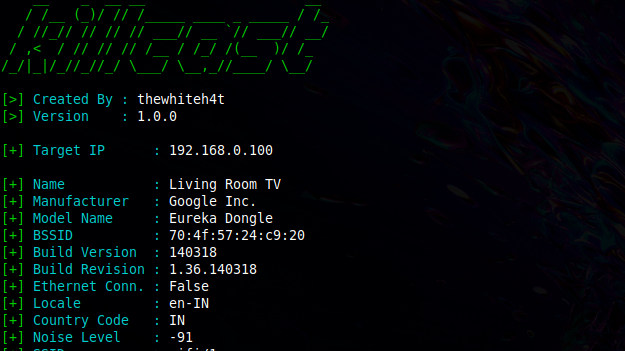
[sc name=”ad_1″] Manipulate Chromecast Devices in your Network. Inspiration – Thousands of Google Chromecast Devices Hijacked to Promote...