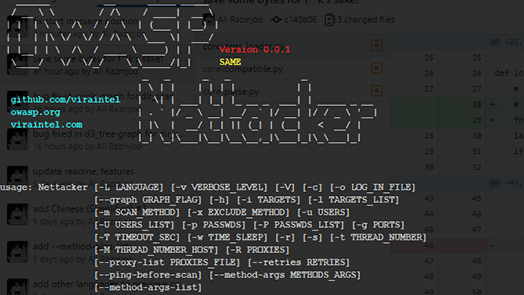
OWASP Nettacker project is created to automate information gathering, vulnerability scanning and eventually generating a report for networks, including...
Search Results For - JSON
The Automated Collection and Enrichment (ACE) platform is a suite of tools for threat hunters to collect data from many endpoints in a network and...
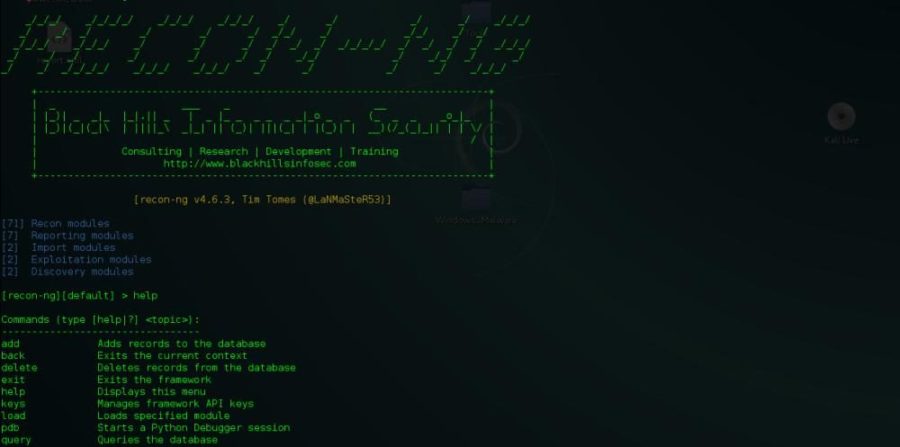
Recon-ng is a full-featured Web Reconnaissance framework written in Python. Complete with independent modules, database interaction, built in convenience...
Wapiti allows you to audit the security of your websites or web applications. It performs “black-box” scans (it does not study the source code) of...
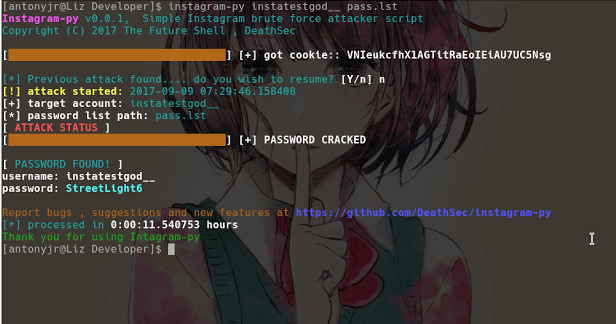
Instagram-Py is a simple python script to perform basic brute force attack against Instagram , this script can bypass login limiting on wrong passwords , so...
BtleJuice is a complete framework to perform Man-in-the-Middle attacks on Bluetooth Smart devices (also known as Bluetooth Low Energy). It is composed of: an...
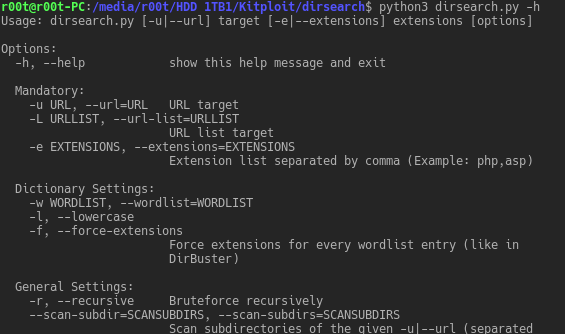
dirsearch is a simple command line tool designed to brute force directories and files in websites. Operating Systems supported Windows XP/7/8/10 GNU/Linux...
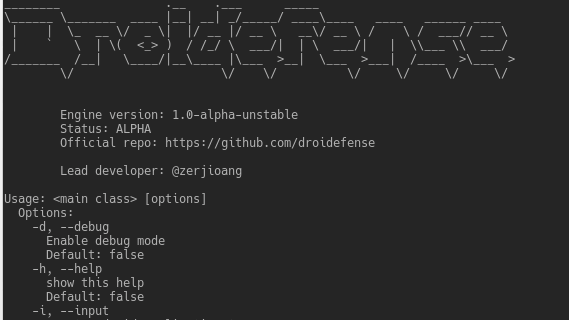
Droidefense (originally named atom: analysis through observation machine)* is the codename for android apps/malware analysis/reversing tool. It was built...
Wazuh is a security detection, visibility, and compliance open source project. It was born as a fork of OSSEC HIDS, later was integrated with Elastic Stack and...
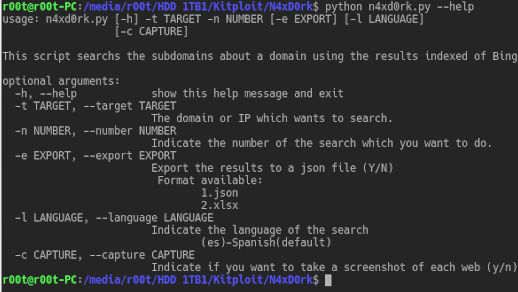
Listing subdomains about the main domain using the technique called Hacking with search engines. Usage usage: n4xd0rk.py [-h] [-d DOMAIN] [-i IP] -o OPTION -n...