A former National Security Agency hacker has admitted to illegally taking highly classified information from the agency’s headquarters, which was later...
Search Results For - Intelligence
Right now, while artificial intelligence is concentrating on profit-generation, natural knowledge has proven to be higher than up to the task of manipulating...
Newly uncovered vulnerabilities in a popular brand of indoor internet-connected cameras could be exploited by attackers in order to gain complete control of...
Apple uses the Tenth Anniversary iPhone X Phone to replace Touch ID. Because the award handset features an edge-to-edge protection and has very slim bezels...
When ironed about how Yahoo failed to realize that 3 billion accounts and not 500 million as first proclaimed were endangered in what was later revealed to be...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
The Trump Organization dismissed the domain names were ever Hacked. But a review of internet credentials by the AP and cybersecurity specialists shows...
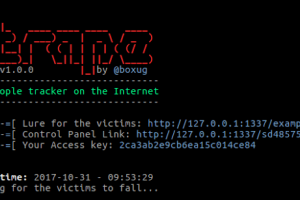
Trape is a recognition tool that allows you to track people, the information you can get is very detailed. We want to teach the world through this, as large...
Cybercriminals decided to use the Search Engine Optimization (SEO) to make their malicious links more widespread in the search results, allowing them to gain...
That was the information of Yann LeCun, the peak of Facebook AI Research, in a conversation with News published on Thursday. While tendencies can learn some...