Looking for an automated malware analysis software? Something like a 1-click solution that doesn’t require any installation or configuration…a...
Search Results For - Injection Attacks
Google has added a new security feature to the latest Linux kernels for Android devices to prevent it against code reuse attacks that allow attackers to...
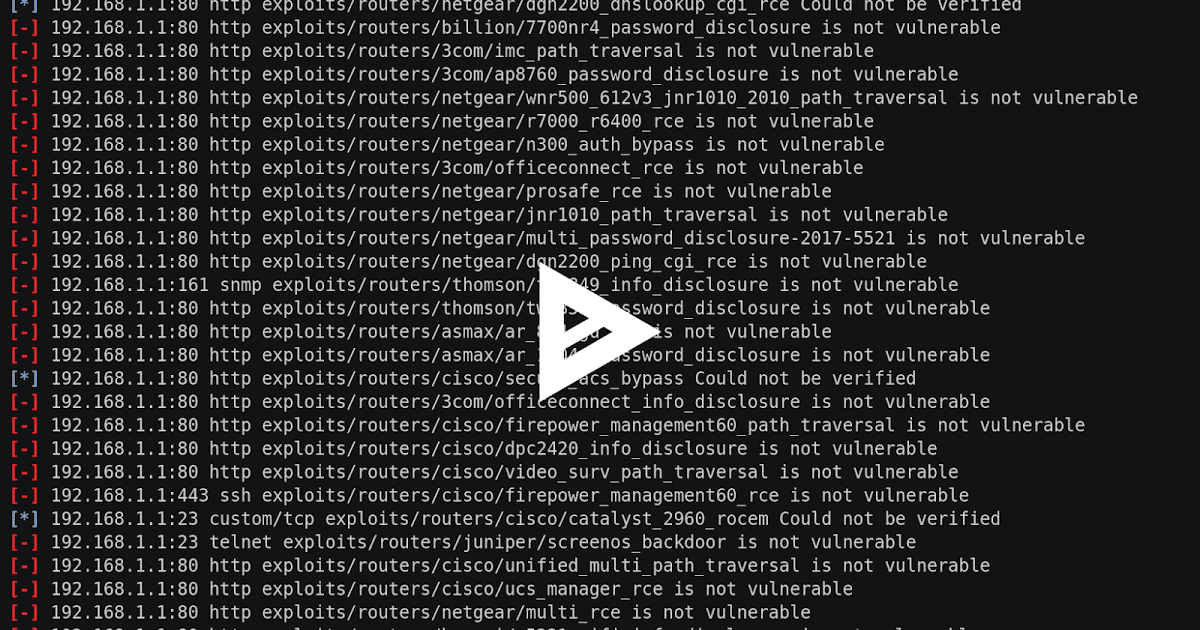
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. It consists of various modules that aids penetration testing...
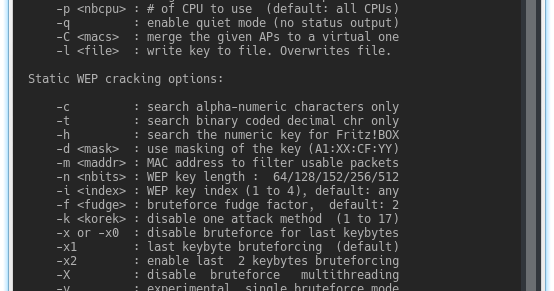
Aircrack-ng is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security: Monitoring: Packet capture and export...
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. It consists of various modules that aids penetration testing...
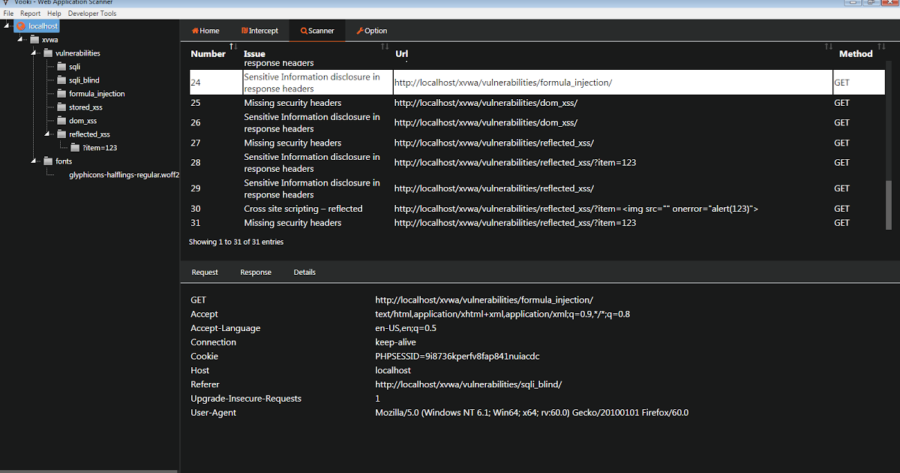
Vooki is a free web application vulnerability scanner. Vooki is a user-friendly tool that you can easily scan any web application and find the vulnerabilities...
p0wnedShell is an offensive PowerShell host application written in C# that does not rely on powershell.exe but runs powershell commands and functions within a...
Magic Unicorn is a simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory. Based on Matthew Graeber’s powershell attacks...
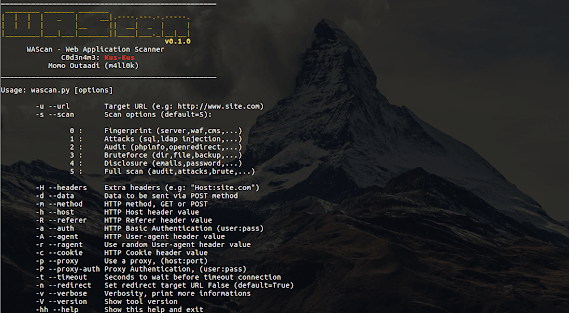
WAScan ((W)eb (A)pplication (Scan)ner) is a Open Source web application security scanner. It is designed to find various vulnerabilities using “black...
Wapiti allows you to audit the security of your websites or web applications. It performs “black-box” scans (it does not study the source code) of...