[sc name=”ad_1″] Shamoon is back… one of the most destructive malware families that caused damage to Saudi Arabia’s largest oil producer in...
Search Results For - Infrastructure
[sc name=”ad_1″] It seems as though not a day goes by without a new story breaking about a high-level cyber attack on a major corporation or...
[sc name=”ad_1″] Earlier this week Dropbox team unveiled details of three critical vulnerabilities in Apple macOS operating system, which...
[sc name=”ad_1″] Google, the FBI, ad-fraud fighting company WhiteOps and a collection of cyber security companies worked together to shut down one...
Pacu is an open source AWS exploitation framework, designed for offensive security testing against cloud environments. Created and maintained by Rhino Security...
All major web browsers, including Google Chrome, Apple Safari, Microsoft Edge, Internet Explorer, and Mozilla Firefox, altogether today announced to soon...
A security researcher has discovered several critical vulnerabilities in one of the most popular embedded real-time operating systems—called FreeRTOS—and its...
Cybersecurity firm FireEye claims to have discovered evidence that proves the involvement of a Russian-owned research institute in the development of the...
Nameles provides an easy to deploy, scalable IVT detection and filtering solution that is proven to detect at a high level of accuracy ad fraud and other types...
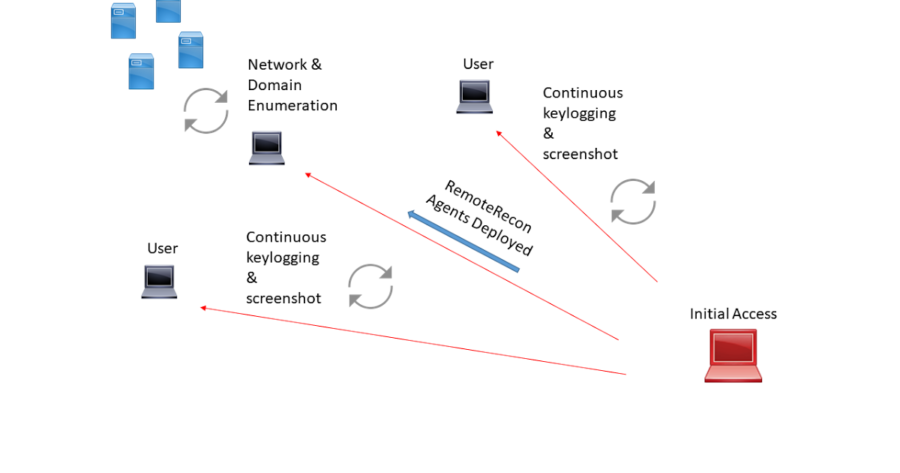
RemoteRecon provides the ability to execute post-exploitation capabilities against a remote host, without having to expose your complete toolkit/agent. Often...