Discovered by UpGuard defense researcher Chris Vickery, the databases were entitled “CENTCOM-backup,” “CENTCOM-archive,” and “pacom-archive.” Based on their...
Search Results For - Information
Security researchers have discovered a new, sophisticated form of malware based on the notorious Zeus banking Trojan that steals more than just bank account...
Now security researchers have discovered that the camera can be silenced and frozen from a script run from any machine within Wi-Fi range, reports News. That...
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...
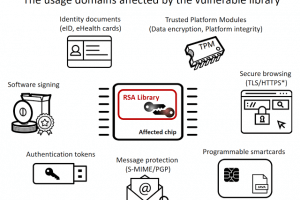
This tool is related to ACM CCS 2017 conference paper #124 Return of the Coppersmith’s Attack: Practical Factorization of Widely Used RSA Moduli. It enables...
A series of recently disclosed critical Bluetooth flaws that affect billions of Android, iOS, Windows and Linux devices have now been discovered in millions of...
Adobe’s latest security update has swatted a total of 67 bugs, some of them critical, in Adobe Flash, Acrobat, and Reader. On Tuesday, the software...
Forever 21 is investigating a potential data breach which may have compromised customer information and payment cards. On Tuesday, the US clothing retailer...
The federal government on Tuesday issued an alert detailing the North Korean government’s use of malware known as FALLCHILL, warning that North Korea has...
Nishang is an open source framework and collection of powerful PowerShell scripts and payloads that you can use during penetration testing audit, post...