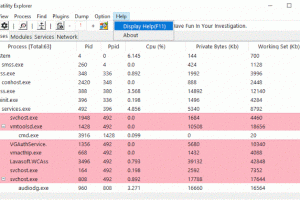
[sc name=”ad_1″] This program allows the user to access a Memory Dump. It can also function as a plugin to the Volatility Framework (). This...
Search Results For - Information
[sc name=”ad_1″] A python based tool for exploiting and managing Android devices via ADB Currently on development Screenrecord Stream Screenrecord...
[sc name=”ad_1″] SecGen creates vulnerable virtual machines, lab environments, and hacking challenges, so students can learn security penetration...
[sc name=”ad_1″] Cloud Security Operations What is Cloud Sniper? Cloud Sniper is a platform designed to manage Security Operations in cloud...
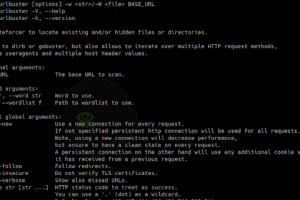
[sc name=”ad_1″] Powerful web directory fuzzer to locate existing and/or hidden files or directories. Similar to dirb or gobuster, but with a lot...
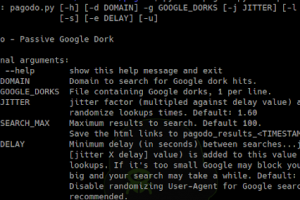
[sc name=”ad_1″] The goal of this project was to develop a passive Google dork script to collect potentially vulnerable web pages and applications...
[sc name=”ad_1″] ReconSpider is most Advanced Open Source Intelligence (OSINT) Framework for scanning IP Address, Emails, Websites, Organizations...
[sc name=”ad_1″] A proof of concept crypto virus to spread user awareness about attacks and implications of ransomwares. Phirautee is written...
[sc name=”ad_1″] Dagobah is an open source tool written in python to automate the internal threat intelligence generation, inventory collection and...
[sc name=”ad_1″] Python module for viewing Portable Executable (PE) files in a tree-view using pefile and PyQt5. Can also be used with IDA Pro to...