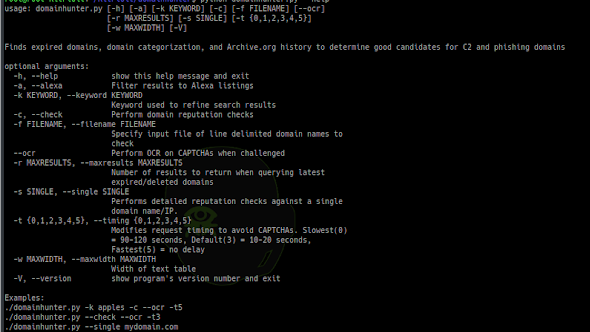
Domain name selection is an important aspect of preparation for penetration tests and especially Red Team engagements. Commonly, domains that were used...
Search Results For - IDA Pro
[sc name=”ad_1″] This is why you should always think twice before opening innocent looking email attachments, especially word and pdf files...
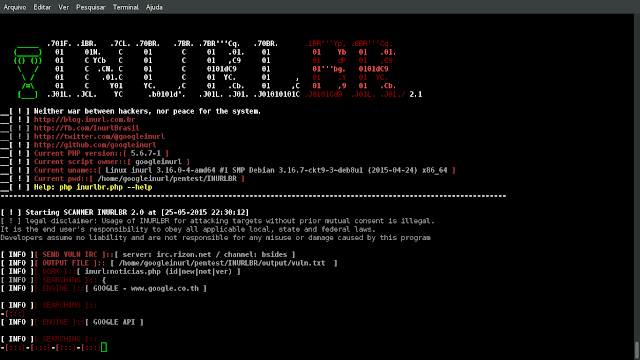
Advanced search in search engines, enables analysis provided to exploit GET / POST capturing emails & urls, with an internal custom validation junction for...
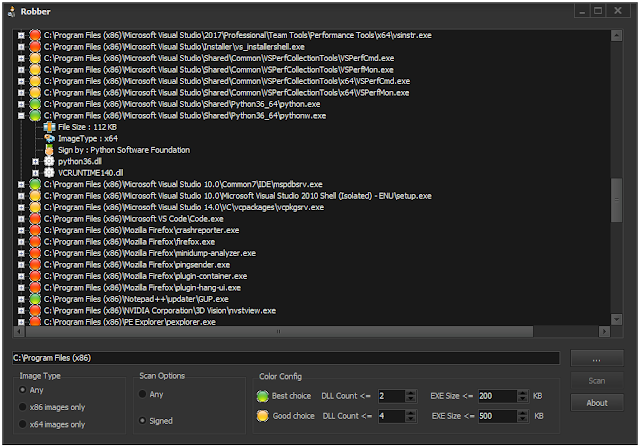
Robber is a free open source tool developed using Delphi XE2 without any 3rd party dependencies. What is DLL hijacking ?! Windows has a search path for DLLs in...
Use this IDA python plugin to scan your binary with yara rules. All the yara rule matches will be listed with their offset so you can quickly hop to them! All...
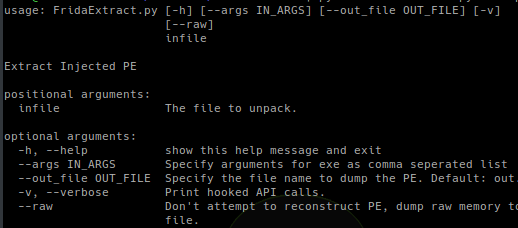
FridaExtract is a Frida.re based RunPE extraction tool. RunPE type injection is a common technique used by malware to hide code within another process. It also...
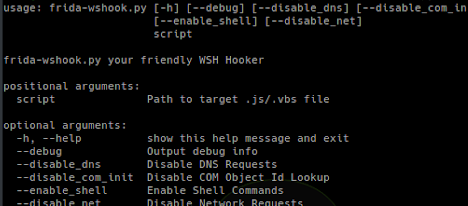
frida-wshook is an analysis and instrumentation tool which uses frida.re to hook common functions often used by malicious script files which are run using...
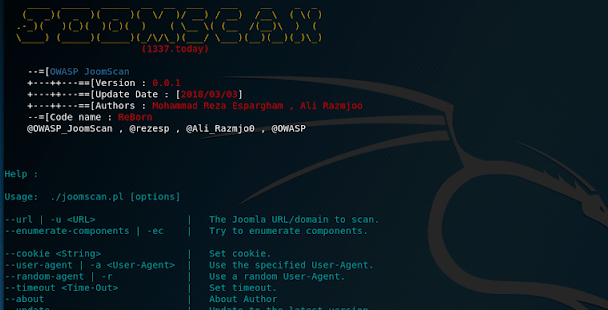
OWASP JoomScan (short for [Joom]la Vulnerability [Scan]ner) is an opensource project in perl programming language to detect Joomla...
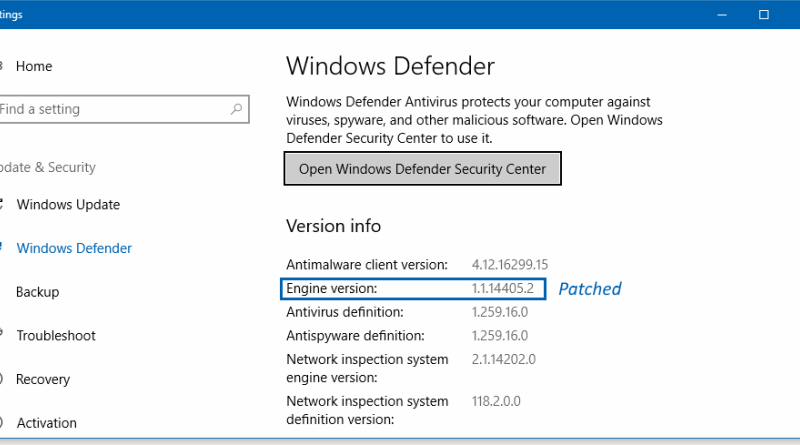
On Wednesday, Microsoft has released a patch for the Microsoft Malware Protection Engine (MPE) to fix a critical severity remote code execution (RCE) flaw in...
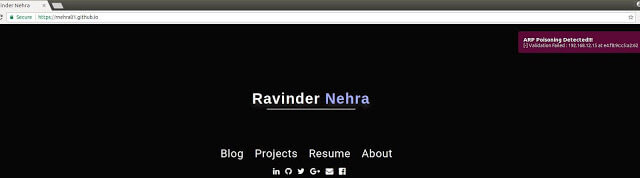
Security Tool to detect arp poisoning attacks. Features Uses a faster approach in detection of arp poisoning attacks compared to passive approaches Detects not...