Rather than heavily protecting backdoors with hardcore packers, many malware authors evade heuristic detections by obfuscating only key portions of an...
Search Results For - IDA Pro
The Port Scan Attack Detector psad is a lightweight system daemon written in is designed to work with Linux iptables/ip6tables/firewalld firewalling code to...
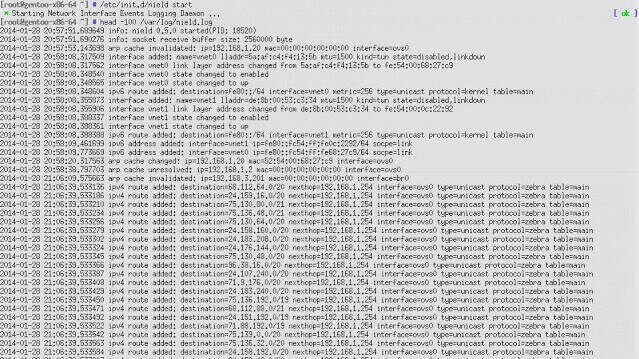
NIELD (Network Interface Events Logging Daemon) is a tool to receive notifications from kernel through netlink socket, and generate logs related to interfaces...
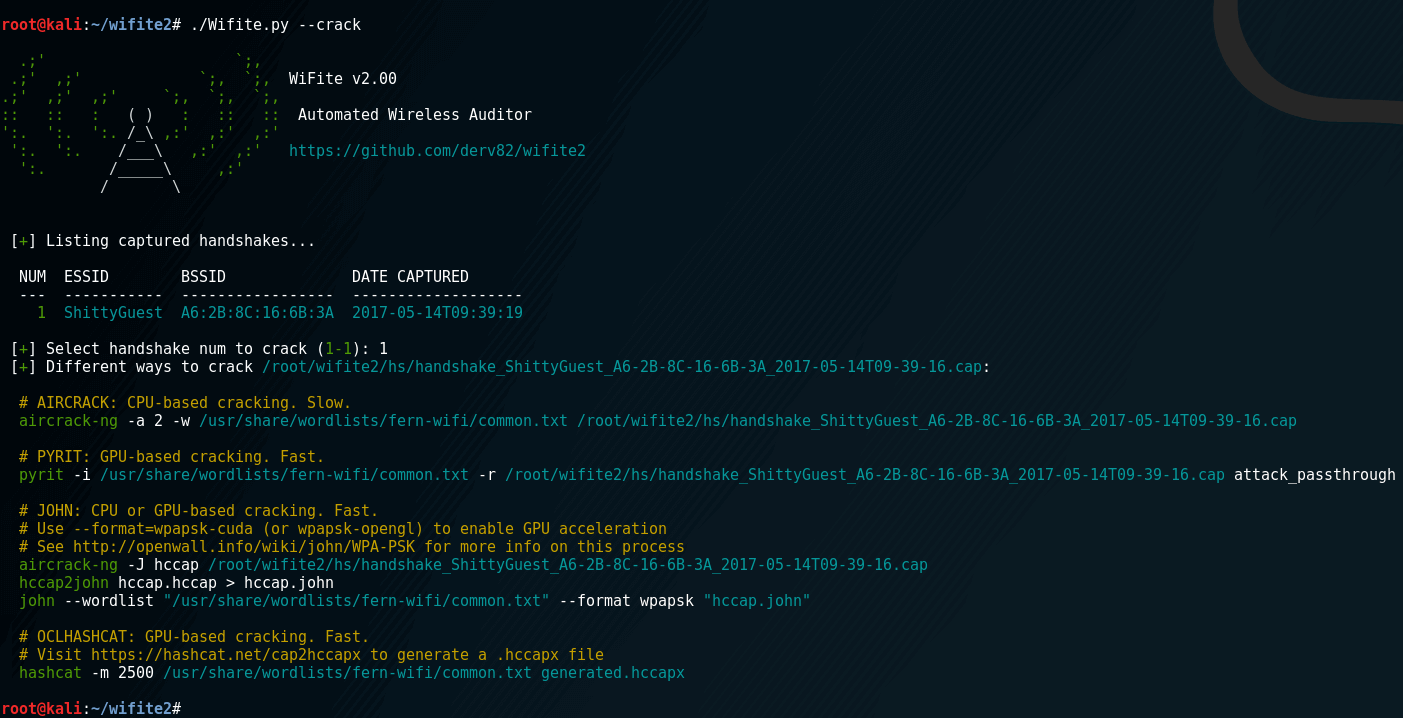
complete re-write of wifite, a Python script for auditing wireless networks. What’s new? Lots of files instead of “one big script”. Cleaner...
objection is a runtime mobile exploration toolkit, powered by Frida. It was built with the aim of helping assess mobile applications and their security posture...
CuckooDroid is an extension of Cuckoo Sandbox the Open Source software for automating analysis of suspicious files. CuckooDroid brigs to cuckoo the...
A British teenager has admitted trying to hack into the computers of senior US government officials, including the director of the CIA and the deputy director...
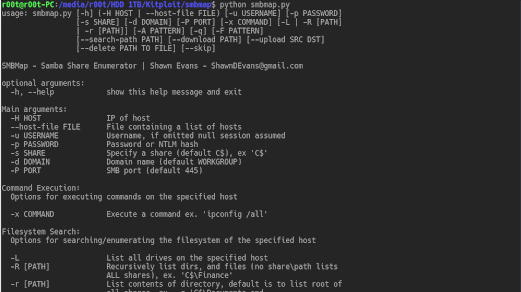
SMBMap allows users to enumerate samba share drives across an entire domain. List share drives, drive permissions, share contents, upload/download...
It seems sophisticated hackers have changed the way they conduct targeted cyber operations—instead of investing in zero-days and developing their malware; some...
The UEFI firmware parser is a simple module and set of scripts for parsing, extracting, and recreating UEFI firmware volumes. This includes parsing modules for...