As the name might suggest AutoSploit attempts to automate the exploitation of remote hosts. Targets are collected automatically as well by employing the Shodan...
Search Results For - IDA Pro
Centralized firewall control provides a centralized way to manage the firewall on multiple servers or loadbalancers running iptables. This way you can quickly...
The malicious software uncovered pornographic ads and attempted to trick users into buying added services, according to Check Point. “We’ve eliminated the apps...
QuarkslaB Dynamic binary Instrumentation (QBDI) is a modular, cross-platform and cross-architecture DBI framework. It aims to support Linux, macOS, Android...
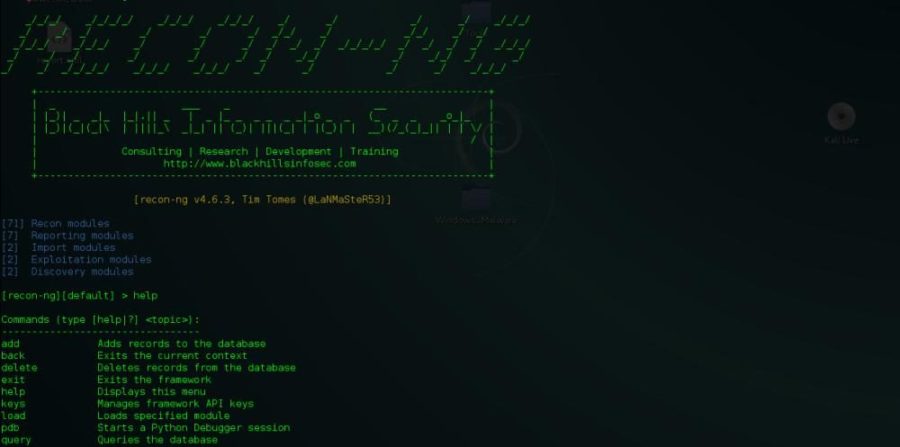
Recon-ng is a full-featured Web Reconnaissance framework written in Python. Complete with independent modules, database interaction, built in convenience...
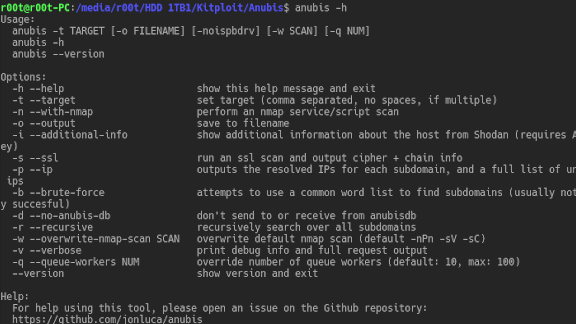
Anubis is a subdomain enumeration and information gathering tool. Anubis collates data from a variety of sources, including HackerTarget, DNSDumpster, x509...
Apple has issued a statement regarding the Meltdown and Spectre vulnerabilities, confirming all Mac systems and iOS devices are affected, but saying there are...
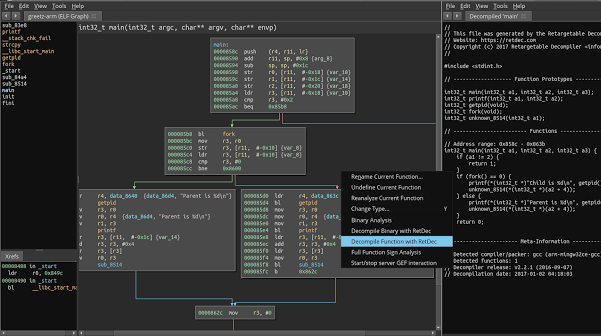
RetDec is a retargetable machine-code decompiler based on LLVM. The decompiler is not limited to any particular target architecture, operating system, or...
The streaming company retweeted its care for the Internet Association’s Friday announced it would “interrupt in a judicial action to save net neutrality...
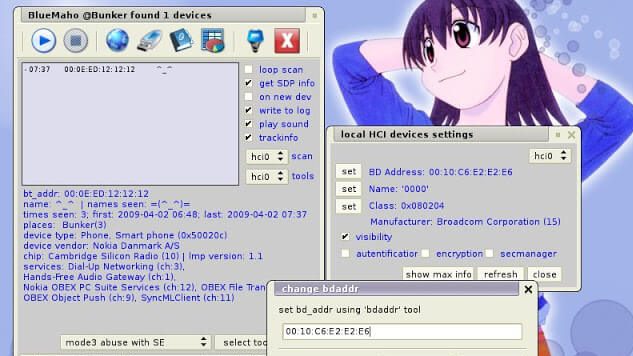
BlueMaho is GUI-shell (interface) for suite of tools for testing security of bluetooth devices. It is freeware, opensource, written on python, uses wxPyhon. It...