Prochunter aims to find hidden process with all userspace and most of the kernelspace rootkits. This tool is composed of a kernel module that prints out all...
Search Results For - Hidden
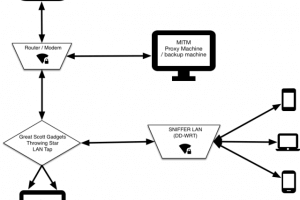
Essentially it’s a WiFi hotspot that is continually collecting all the packets transmitted across it. All connected clients’ HTTPS communications are subjected...
The federal government on Tuesday issued an alert detailing the North Korean government’s use of malware known as FALLCHILL, warning that North Korea has...
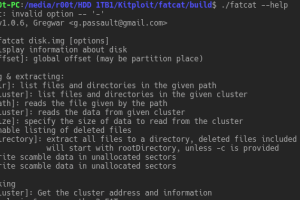
This tool is designed to manipulate FAT filesystems, in order to explore, extract, repair, recover and forensic them. It currently supports FAT12, FAT16 and...
Today, 9 November 2017, WikiLeaks publishes the source code and development logs to Hive, a major component of the CIA infrastructure to control its malware...
Security GNU/Linux distribution designed with cloud pentesting and IoT security in mind. It includes a full portable laboratory for security and digital...
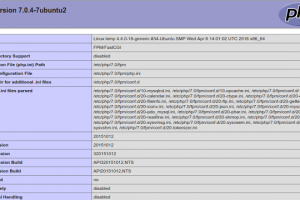
Check current PHP configuration for potential security flaws. Simply access this file from your webserver or run on CLI. Author This software was written by...
Cybercriminals are known to take advantage of everything that’s popular among people in order to spread malware, and Google’s official Play Store...
Use nmap to scan hidden “onion” services on the Tor network. Minimal image based on alpine, using proxychains to wrap nmap. Tor and dnsmasq are run as daemons...
Canvas fingerprinting relies on websites meaning able to receive data from HTML canvas details calmly. In future, Firefox users will be required to give their...