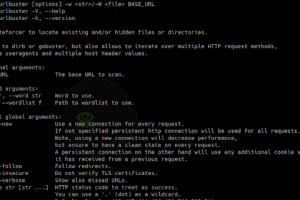
[sc name=”ad_1″] Powerful web directory fuzzer to locate existing and/or hidden files or directories. Similar to dirb or gobuster, but with a lot...
Search Results For - Hidden
[sc name=”ad_1″] Tor is free and open-source software for enabling anonymous communication. The name derived from the acronym for the original...
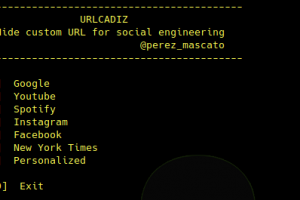
[sc name=”ad_1″] A simple script to generate a hidden url for social engineering. Legal disclaimer: Usage of URLCADIZ for attacking targets without...
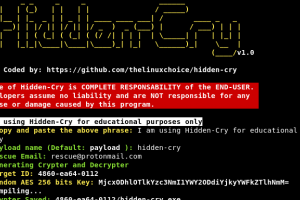
[sc name=”ad_1″] Windows Crypter/Decrypter Generator with AES 256 bits key Features: Works on WAN: Port Forwarding by Serveo.net Fully Undetectable...
[sc name=”ad_1″] FOCA (Fingerprinting Organizations with Collected Archives) FOCA is a tool used mainly to find metadata and hidden information in...
[sc name=”ad_1″] Cybersecurity researchers have discovered a new zero-day vulnerability in Adobe Flash Player that hackers are actively exploiting...
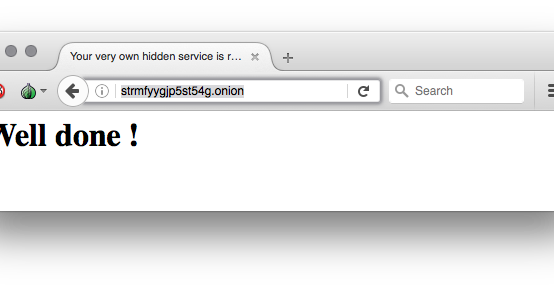
Easily run a hidden service inside the Tor network with this container Generate the skeleton configuration for you hidden service, replace for your hidden...
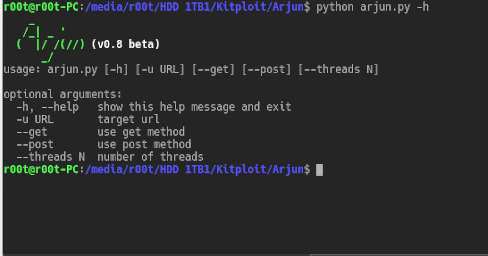
Arjun is a python script for finding hidden GET & POST parameters using regex and bruteforce. Dependencies requests threading Usages Here’s how you...
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
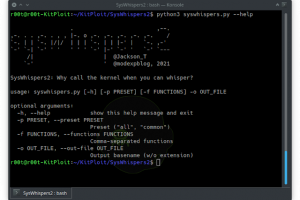
[sc name=”ad_1″] SysWhispers helps with evasion by generating header/ASM files implants can use to make direct system calls. All core syscalls are...