[sc name=”ad_1″] A team of cybersecurity researchers from the University of New Haven yesterday released a video demonstrating how vulnerabilities...
Search Results For - Hacking
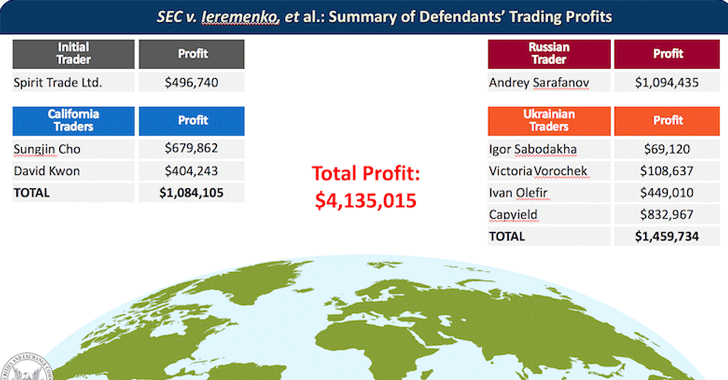
[sc name=”ad_1″] The U.S. authorities have charged two Ukrainian hackers for hacking into the Securities and Exchange Commission’s EDGAR...
[sc name=”ad_1″] The US Department of Justice on Thursday charged two Chinese hackers associated with the Chinese government for hacking numerous...
Welcome to our fourth and final release of 2018, Kali Linux 2018.4, which is available for immediate download. This release brings kernel up to version 4.18...
A 21-year-old Kentucky man who previously pleaded guilty to developing, marketing, and selling an infamous remote access trojan (RAT) called LuminosityLink has...
M$ Windows Hacking Pack =========== Tools here are from different sources. The repo is generally licensed with WTFPL, but some content may be not (eg...
Hacking requires a lot of brainstorming since you need a robust machine that will not lag or run out of resources during working. Hacking involves DDOS a...
[sc name=”ad_1″] Hacking a Wi-Fi network using Kali Linux needs a wireless card that support monitor mode and packet injection. Not all wireless...
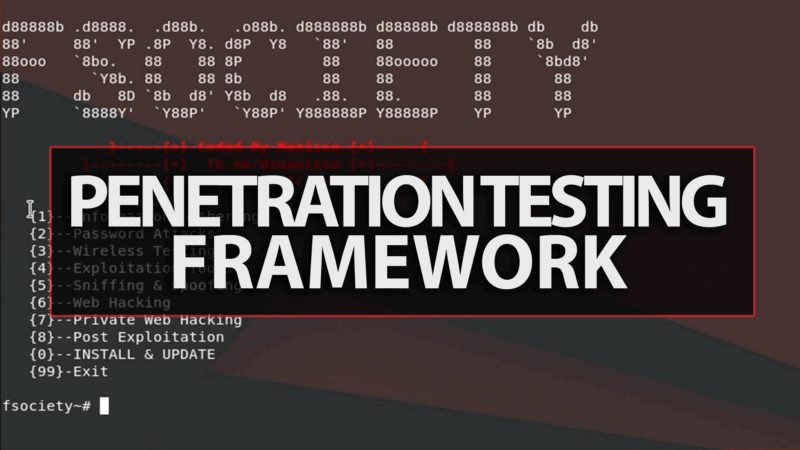
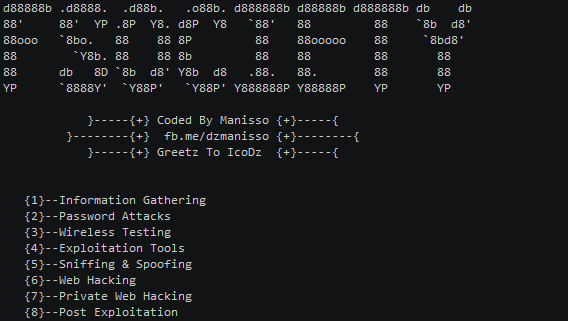
A Penetration Testing Framework, you will have every script that a hacker needs Fsociety: Menu Information Gathering Password Attacks Wireless Testing...
A Penetration Testing Framework , you will have every script that a hacker needs Menu Information Gathering Password Attacks Wireless Testing Exploitation...