A security researcher has discovered several critical vulnerabilities in one of the most popular embedded real-time operating systems—called FreeRTOS—and its...
Search Results For - Hackers
Microsoft Windows built-in anti-malware tool, Windows Defender, has become the very first antivirus software to have the ability to run inside a sandbox...
When it comes to security updates, Android is a real mess. Even after Google timely rolls out security patches for its Android platform, a major part of the...
Cybersecurity firm FireEye claims to have discovered evidence that proves the involvement of a Russian-owned research institute in the development of the...
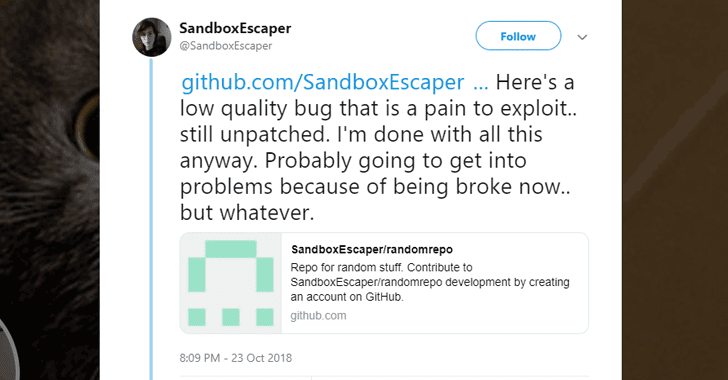
A security researcher with Twitter alias SandboxEscaper—who two months ago publicly dropped a zero-day exploit for Microsoft Windows Task Scheduler—has...
Despite countless examples to the contrary, many people still toss cryptocurrency and criminal activity into the same bucket. But is this born out of ignorance...
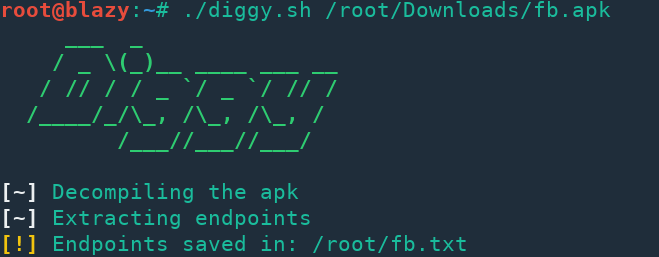
Diggy can extract endpoints/URLs from apk files. It saves the result into a txt file for further processing. Dependencies apktool Usage ./diggy.sh...
Hacking requires a lot of brainstorming since you need a robust machine that will not lag or run out of resources during working. Hacking involves DDOS a...
XSStrike is an advanced XSS detection and exploitation suite. It has a powerful fuzzing engine and provides zero false positive result using fuzzy matching...
Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also...