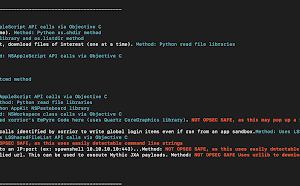
[sc name=”ad_1″] MacC2 is a macOS post exploitation tool written in python that uses Objective C calls or python libraries as opposed to command...
Search Results For - Generator
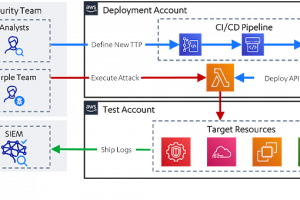
[sc name=”ad_1″] Leonidas is a framework for executing attacker actions in the cloud. It provides a YAML-based format for defining cloud attacker...
[sc name=”ad_1″] Based on pywebfuzz, Py3webfuzz is a Python3 module to assist in the identification of vulnerabilities in web applications, Web...
[sc name=”ad_1″] “”” What is this register used for? Hmm.. I’ll just rename it to veryuniquename, do a textual search, and...
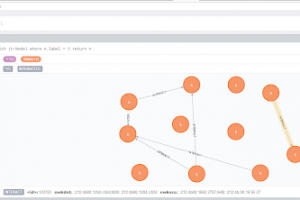
[sc name=”ad_1″] IoTMap is a tool that models IoT networks using one or multiple protocols simultaneously. This is work in progress, as a part of a...
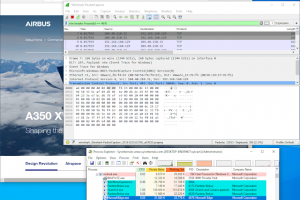
[sc name=”ad_1″] Wireshark plugin to work with Event Tracing for Windows Microsoft Message Analyzer is being retired and its download packages were...
[sc name=”ad_1″] HTTP-revshell is a tool focused on redteam exercises and pentesters. This tool provides a reverse connection through the http/s...
[sc name=”ad_1″] A security framework for enterprises and Red Team personnel, supports CobaltStrike’s penetration testing of other...
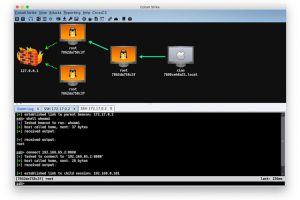
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...
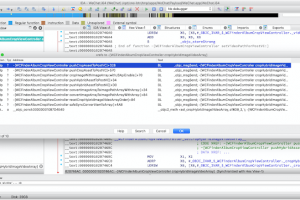
[sc name=”ad_1″] iblessing iblessing is an iOS security exploiting toolkit, it mainly includes application information collection, static analysis...