[sc name=”ad_1″] The United States Department of Justice (DoJ) announced Wednesday its effort to “map and further disrupt” a botnet...
Search Results For - Firewall
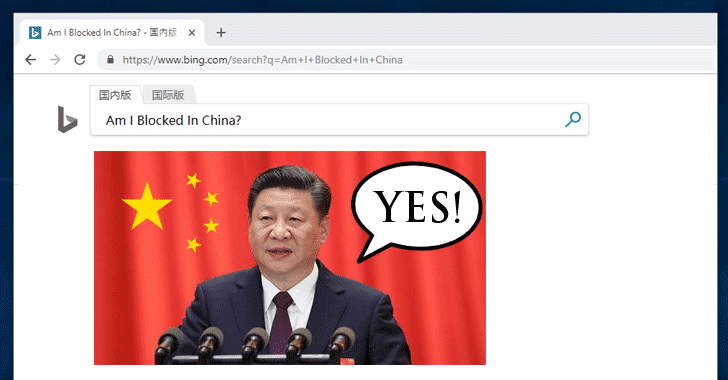
[sc name=”ad_1″] China has blocked Microsoft-owned search engine Bing, the company confirmed after receiving complaints from users throughout the...
[sc name=”ad_1″] A massive government data belonging to the Oklahoma Department of Securities (ODS) was left unsecured on a storage server for at...
[sc name=”ad_1″] A California-based Voice-Over-IP (VoIP) services provider VOIPO has accidentally left tens of gigabytes of its customer data...
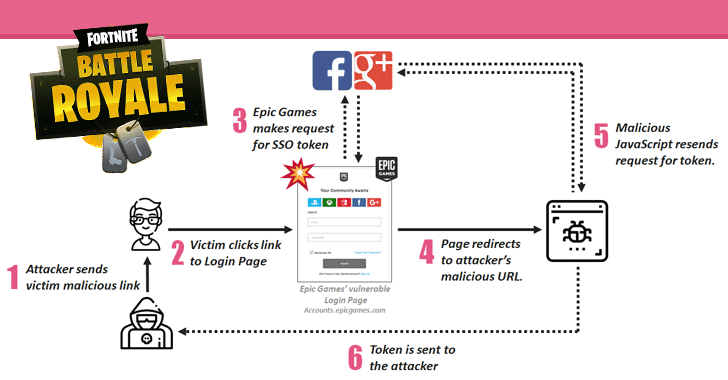
[sc name=”ad_1″] Check Point researchers have discovered multiple security vulnerabilities in Fortnite, a massively popular online battle game, one...
[sc name=”ad_1″] It seems as though not a day goes by without a new story breaking about a high-level cyber attack on a major corporation or...
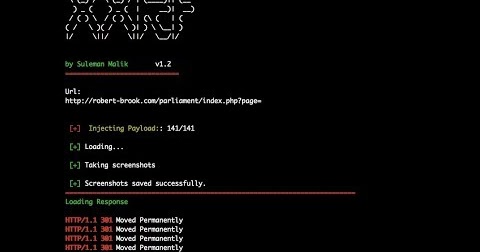
Looking for an automated malware analysis software? Something like a 1-click solution that doesn’t require any installation or configuration…a...
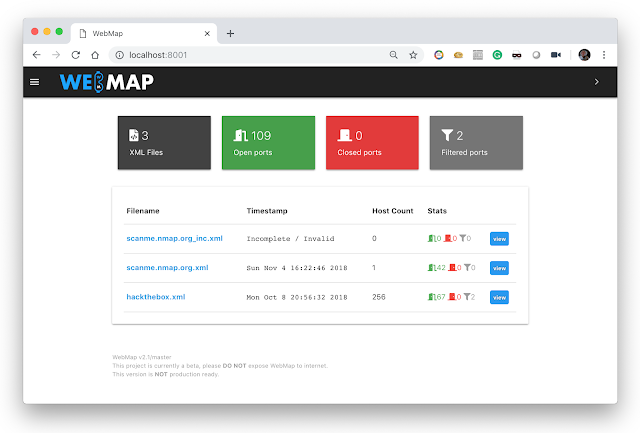
A Web Dashbord for Nmap XML Report Usage You should use this with docker, just by sending this command: $ mkdir /tmp/webmap $ docker run -d --name webmap -h...
What is SSRF vulnerability? Server Side Request Forgery (SSRF) is a type of vulnerability class where attacker sends crafted request from a vulnerable web...
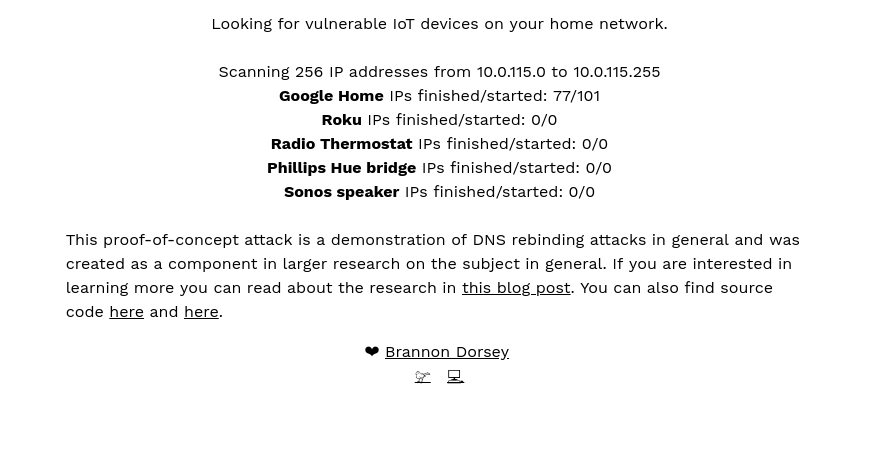
DNS Rebind Toolkit is a frontend JavaScript framework for developing DNS Rebinding exploits against vulnerable hosts and services on a local area...