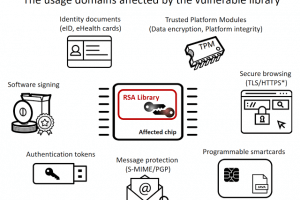
This tool is related to ACM CCS 2017 conference paper #124 Return of the Coppersmith’s Attack: Practical Factorization of Widely Used RSA Moduli. It enables...
Search Results For - Fingerprint
Apple uses the Tenth Anniversary iPhone X Phone to replace Touch ID. Because the award handset features an edge-to-edge protection and has very slim bezels...
Turns out all they ought to do was ask Apple for help. In a comment the tech titan has issued to the media, it said it “quickly reached out to the FBI after...
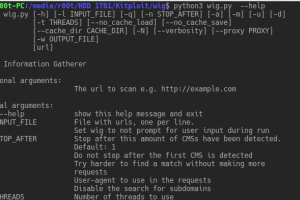
wig is a web application information gathering tool, which can identify numerous Content Management Systems and other administrative applications. The...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
Striker is an offensive information and vulnerability scanner. Features Just supply a domain name to Striker and it will automatically do the following for...
Exitmap is a fast and modular Python-based scanner for Tor exit relays. Exitmap modules implement tasks that are run over (a subset of) all exit relays. If you...
Canvas fingerprinting is a byproduct of the HTML5 Canvas technology that all browser inventors attached to their browsers. As is the problem with many...
81 percent of data breaks last year involved weak, default or stolen passwords, and phishing attacks have advanced 65 percent year-on-year. Protecting online...
Studies on the topic of in-browser miners have been going on the Chromium project’s bug tracker since mid-September when Coinhive, the first launched. To...