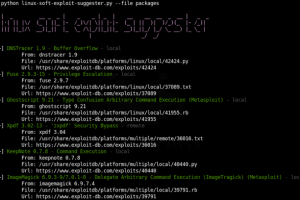
linux-soft-exploit-suggester finds exploits for all vulnerable software in a system helping with the privilege escalation. It focuses on software packages...
Search Results For - File Include
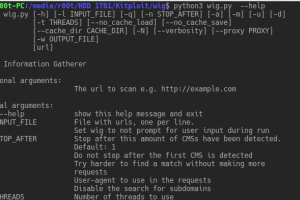
wig is a web application information gathering tool, which can identify numerous Content Management Systems and other administrative applications. The...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
The Trump Organization dismissed the domain names were ever Hacked. But a review of internet credentials by the AP and cybersecurity specialists shows...
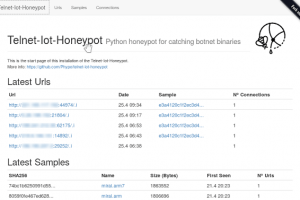
This project implements a python telnet server trying to act as a honeypot for IoT Malware which spreads over horribly insecure default passwords on telnet...
Critically, both OS updates address the KRACK Wi-Fi vulnerability for any devices. It is a dangerous vulnerability in the WPA2 Wi-Fi assurance standard that...
FireEye’s Innovation and Custom Engineering (ICE) team released a tool called GoCrack that allows red teams to efficiently manage password cracking tasks...
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These changes are the next...
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
Exitmap is a fast and modular Python-based scanner for Tor exit relays. Exitmap modules implement tasks that are run over (a subset of) all exit relays. If you...