Right now, while artificial intelligence is concentrating on profit-generation, natural knowledge has proven to be higher than up to the task of manipulating...
Search Results For - Facebook
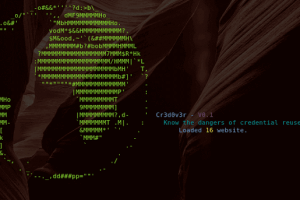
Your best friend in credential reuse attacks. Cr3dOv3r simply you give it an email then it does two simple jobs (but useful) : Search for public leaks for the...
Cybercriminals are known to take advantage of everything that’s popular among people in order to spread malware, and Google’s official Play Store...
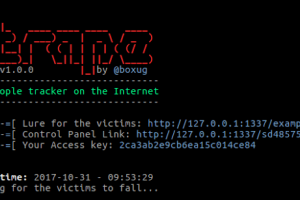
Trape is a recognition tool that allows you to track people, the information you can get is very detailed. We want to teach the world through this, as large...
Are you a proud iPhone owner? If yes, this could freak you up. Trust me! Your iPhone has a serious privacy concern that allows iOS app developers to take your...
Use nmap to scan hidden “onion” services on the Tor network. Minimal image based on alpine, using proxychains to wrap nmap. Tor and dnsmasq are run as daemons...
According to various cybersecurity firms, the growing virus is dubbed “BadRabbit” and is a form of ransomware that bolts down machines and requires bitcoin...
81 percent of data breaks last year involved weak, default or stolen passwords, and phishing attacks have advanced 65 percent year-on-year. Protecting online...
Many internet giants offer security measures like two-factor authentication (which you should really use) to keep your account safe from hackers. But there are...
Ever been wondering if your ISP is hijacking your DNS traffic? Ever observed any misbehavior with your DNS responses? Ever been redirected to wrong address and...