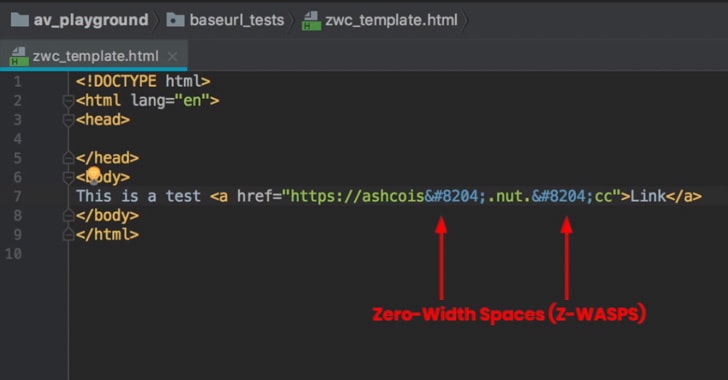
[sc name=”ad_1″] Security researchers have discovered three vulnerabilities in Systemd, a popular init system and service manager for most Linux...
Search Results For - Exploits
[sc name=”ad_1″] Security researchers have been warning about a simple technique that cybercriminals and email scammers are already being using in...
[sc name=”ad_1″] Shodan is a search engine on the internet where you can find interesting things all over the world. For example, we can find...
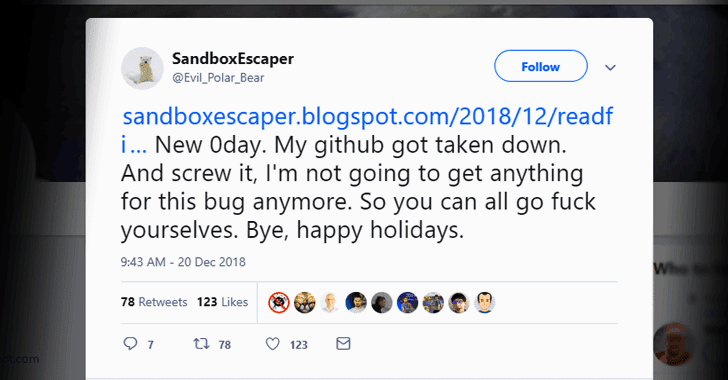
[sc name=”ad_1″] A security researcher with Twitter alias SandboxEscaper today released proof-of-concept (PoC) exploit for a new zero-day...
[sc name=”ad_1″] Microsoft today, on its year-end December Patch Tuesday, released security updates to patch a total 39 vulnerabilities its Windows...
[sc name=”ad_1″] Adobe is closing out this year with its December Patch Tuesday update to address a massive number of security vulnerabilities for...
[sc name=”ad_1″] This is why you should always think twice before opening innocent looking email attachments, especially word and pdf files...
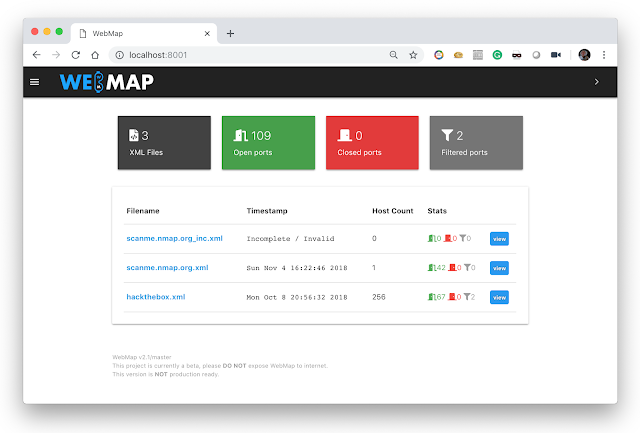
A Web Dashbord for Nmap XML Report Usage You should use this with docker, just by sending this command: $ mkdir /tmp/webmap $ docker run -d --name webmap -h...
Advanced search in search engines, enables analysis provided to exploit GET / POST capturing emails & urls, with an internal custom validation junction for...
The main purpose of the tool is automating (PasteJacking/Clipboard poisoning/whatever you name it) attack with collecting all the known tricks used in this...