[sc name=”ad_1″] Popular enterprise software company Citrix that provides services to the U.S. military, the FBI, many U.S. corporations, and...
Search Results For - Exploits
[sc name=”ad_1″] The Metasploit Project is a computer security project that provides information on vulnerabilities, helping in the development of...
[sc name=”ad_1″] It’s not just the critical Drupal vulnerability that is being exploited by in the wild cybercriminals to attack vulnerable...
[sc name=”ad_1″] Cybercriminals have actively started exploiting an already patched security vulnerability in the wild to install cryptocurrency...
[sc name=”ad_1″] Developers of Drupal—a popular open-source content management system software that powers millions of websites—have released the...
[sc name=”ad_1″] A serious security vulnerability has been discovered in the core runC container code that affects several open-source container...
[sc name=”ad_1″] Cybersecurity researchers have discovered a way to hide malicious code in Intel SGX enclaves, a hardware-based memory encryption...
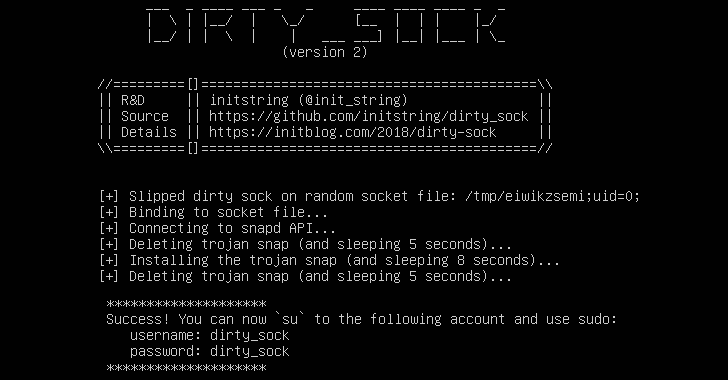
[sc name=”ad_1″] Ubuntu and some other Linux distributions suffer from a severe privilege escalation vulnerability that could allow a local...
[sc name=”ad_1″] If the connectivity and security of your organization rely on Cisco RV320 or RV325 Dual Gigabit WAN VPN routers, then you need to...
[sc name=”ad_1″] It is 2019, and millions of computers still either have at least one outdated application installed or run outdated operating...