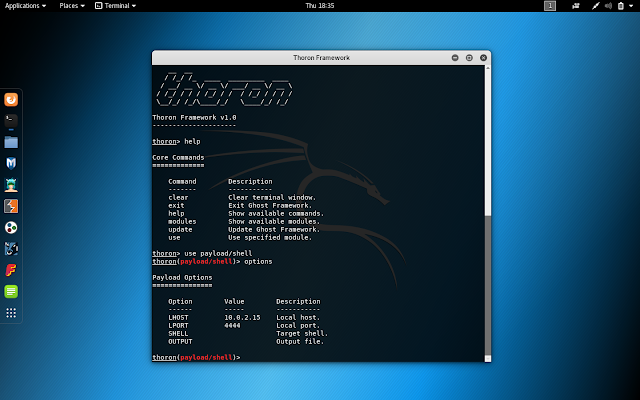
[sc name=”ad_1″] About Thoron Framework Thoron Framework is a Linux post-exploitation framework that exploit Linux tcp vulnerability to get shell...
Search Results For - Exploitation
[sc name=”ad_1″] Lockdoor Framework : A Penetration Testing Framework With Cyber Security Resources. 09/2019 : 1.0Beta Information Gathring Tools...
[sc name=”ad_1″] FAT is a toolkit built in order to help security researchers analyze and identify vulnerabilities in IoT and embedded device...
[sc name=”ad_1″] This tool launches attack on k8s cluster from within. That means you already need to have an access with permission to deploy pods...
[sc name=”ad_1″] A File Inclusion & Directory Traversal fuzzing, enumeration & exploitation tool. FDsploit menu: $ python fdsploit.py -h...
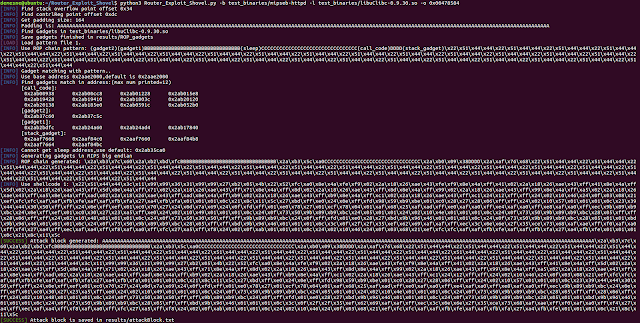
[sc name=”ad_1″] Automated Application Generation for Stack Overflow Types on Wireless Routers. Router exploits shovel is an automated application...
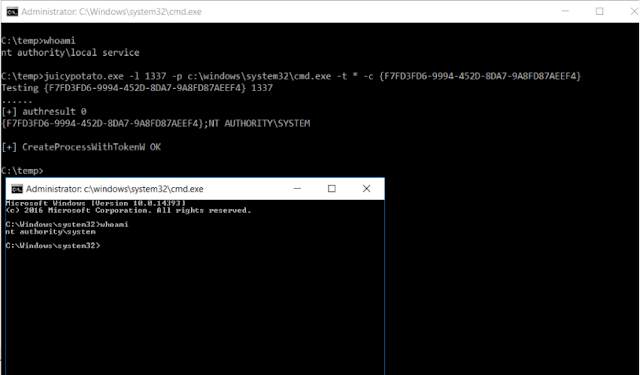
[sc name=”ad_1″] A sugared version of RottenPotatoNG, with a bit of juice, i.e. another Local Privilege Escalation tool, from a Windows Service...
[sc name=”ad_1″] It’s time for another batch of “Patch Tuesday” updates from Microsoft. Microsoft today released its March 2019...
[sc name=”ad_1″] Adobe users would feel lighter this month, as Adobe has released patches for just two security vulnerability in its March Security...
[sc name=”ad_1″] Security researchers have finally, with “high confidence,” linked a previously discovered global cyber espionage...