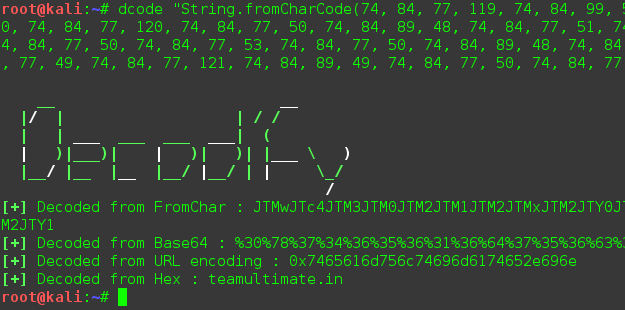
Decodify can detect and decode encoded strings, recursively. Its currently in beta phase. Lets take this string : teamultimate.in and encode it with Hex, URL...
Search Results For - Encryption
A breach of Forever 21 left consumer payment card data exposed to hackers, the retailer verified Thursday. The business didn’t specify how many customers had...
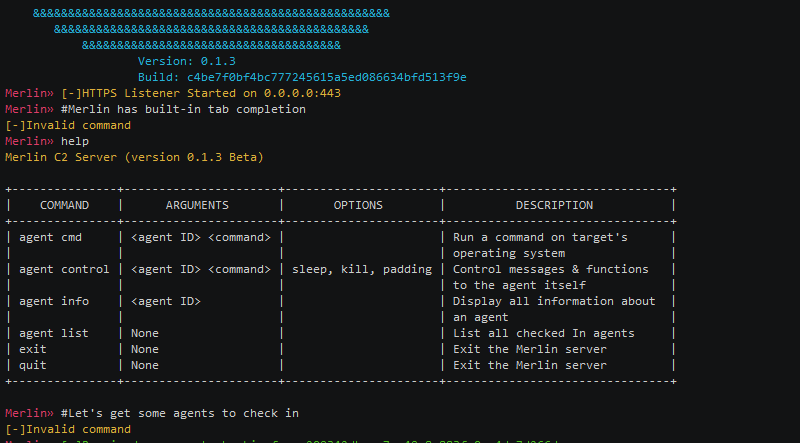
Merlin is a cross-platform post-exploitation framework that leverages HTTP/2 communications to evade inspection. HTTP/2 is a relatively new protocol that...
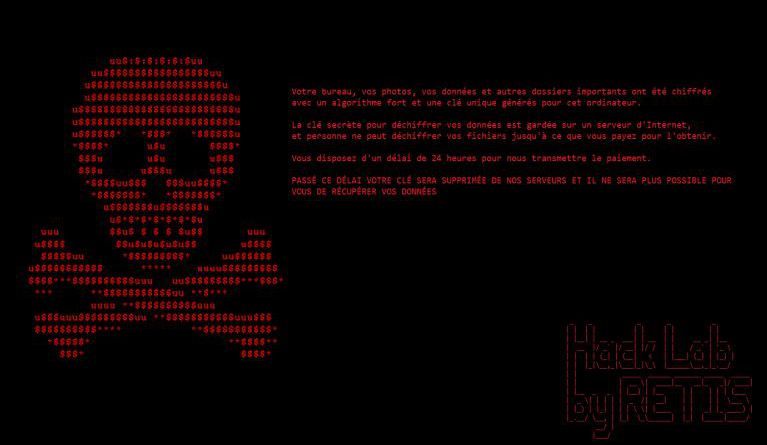
A security researcher has discovered a ransomware called Retis, which is a ransomware-type virus that secretly infiltrates the system. Shortly after executed...
Security GNU/Linux distribution designed with cloud pentesting and IoT security in mind. It includes a full portable laboratory for security and digital...
MoneyTaker hackers, A group of Russian hackers, has been laying waste to banks internationally and locally. In the past 18 months, this group has stolen a...
Some work has been already published regarding the subject of cryptograhic keys security within DRAM. Basically, we need to find something that looks like a...
Amber is a proof of concept packer, it can pack regularly compiled PE files into reflective PE files that can be used as multi stage infection payloads. If you...
What this tool does is taking a file (any type of file), encrypt it, and embed it into an HTML file as ressource, along with an automatic download routine...
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...