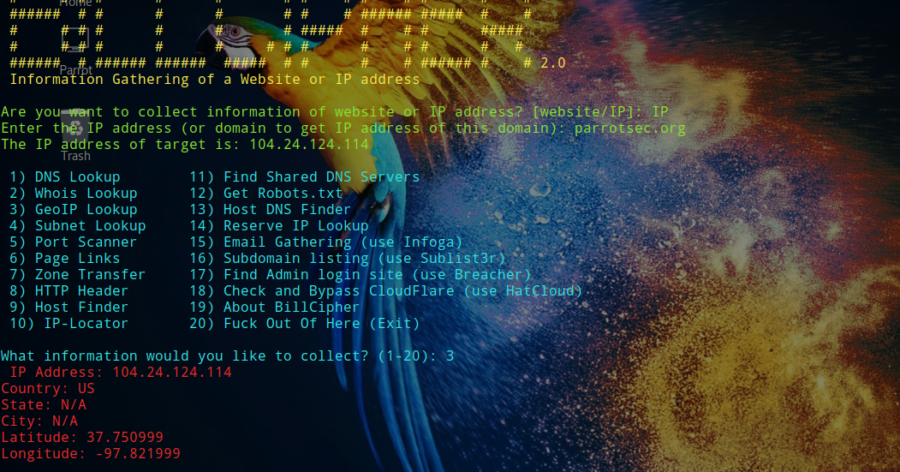
Information Gathering tool for a Website or IP address, use some ideas from Devploit. BillCipher can work in any operating system if they have and support...
Search Results For - Encoding
Interview: Aragon’s Luis Cuende on Blockchain Governance & Digital Jurisdictions Author: Bennett Garner Bennett Garner: You’ve said “humans enforce...
Hacking requires a lot of brainstorming since you need a robust machine that will not lag or run out of resources during working. Hacking involves DDOS a...
Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also...
Raspberry Pi 3 Model B+ is now on sale for $35 (the same price as the existing Raspberry Pi 3 Model B), featuring: A 1.4GHz 64-bit quad-core ARM Cortex-A53 CPU...
FIDO U2F Security key is a personal encryption method which individualizes your online security by providing a secondary layer of encryption via the USB port...
[sc name=”ad_1″] Hacking a Wi-Fi network using Kali Linux needs a wireless card that support monitor mode and packet injection. Not all wireless...
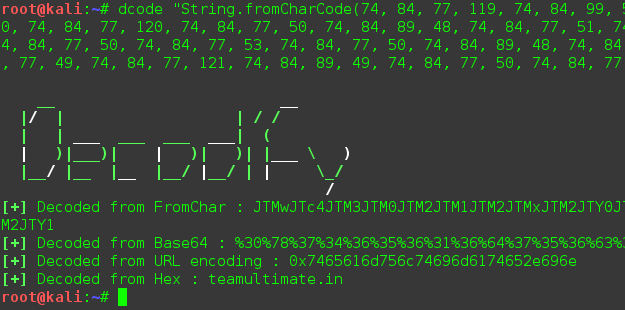
Decodify can detect and decode encoded strings, recursively. Its currently in beta phase. Lets take this string : teamultimate.in and encode it with Hex, URL...
The macro_pack is a tool used to automatize obfuscation and generation of MS Office documents for pentest, demo, and social engineering assessments. The goal...
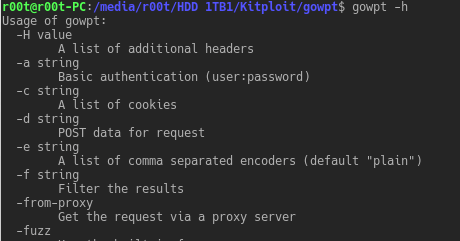
GOWPT is the younger brother of wfuzz a swiss army knife of WAPT, it allow pentester to perform huge activity with no stress at all, just configure it and...