The 2016 election hack is back in the news. With great efforts, a Russian hacker was arrested and upon interrogation, he revealed that he was hired by the...
Search Results For - Emails
Your best friend in credential reuse attacks. Cr3dOv3r simply you give it an email then it does two simple jobs (but useful) : Search for public leaks for the...
The firm looked at nearly 70 million emails sent during October from 5,000 different .gov origin domains preserved by Proofpoint, the company’s VP of Email...
Your best friend in credential reuse attacks. Cr3dOv3r simply you give it an email then it does two simple jobs (but useful) : Search for public leaks for the...
A robust Phishing Framework with a full featured CLI interface. The project was born out necessity through of years of engagements with tools that just didn’t...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
The Trump Organization dismissed the domain names were ever Hacked. But a review of internet credentials by the AP and cybersecurity specialists shows...
Striker is an offensive information and vulnerability scanner. Features Just supply a domain name to Striker and it will automatically do the following for...
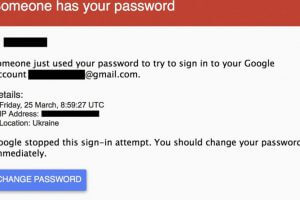
Wesley Neelen (security researcher) has received a phishing email that seems to be from the legal online Ethereum wallet site Myetherwallet.com. Cybercriminals...