Striker is an offensive information and vulnerability scanner. Features Just supply a domain name to Striker and it will automatically do the following for...
Search Results For - Email
The cryptocurrency has had a bullish streak completely the week following the CME’s statement that it will introduce bitcoin expectations contracts. According...
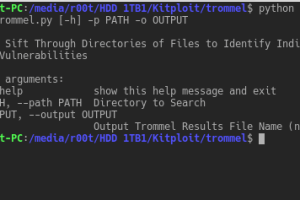
TROMMEL sifts through directories of files to identify indicators that may contain vulnerabilities. TROMMEL identifies the following indicators related to:...
Across the Internet, hundreds of thousands of sites rely on Google’s reCaptcha system for defense against bots (in fact, Devpost uses reCaptcha when creating a...
Tweep is an advanced Twitter scraping tool written in python that allows for scraping Tweets and pictures from Twitter profiles without using Twitter’s...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
News reported in June that McAfee was amongst several Western technology organizations that had acceded in recent years to larger demands by Moscow for access...
The flaw was discovered by researchers from Check Point in the user authentication method between the SmartThinQ portable app and LG’s back-end platform. This...
LG has updated its software after security researchers spotted a flaw that allowed them to gain control of devices like refrigerators, ovens, dishwashers, and...