One of the biggest names in IT industry, Intel, has verified a report stating that some microprocessors have been built containing flaws in their design...
Search Results For - Discovery
The PowerUpSQL module includes functions that support SQL Server discovery, auditing for common weak configurations, and privilege escalation on scale. It is...
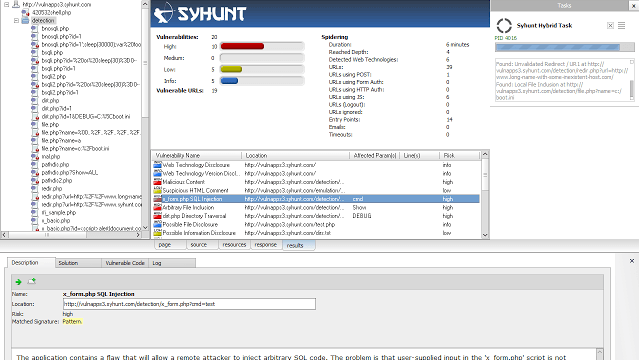
Syhunt ScanTools 6.0 adds advanced fingerprinting capabilities, enhanced spidering, injection and code scan capabilities, and a large number of improved checks...
The researchers demanded data left visible entered names, phone numbers, locations and Google queries. The chief of the Israeli company back the app confirmed...
Features Auto VoIP/UC penetration test Report generation Performance RFC compliant SIP TLS and IPv6 support SIP over websockets (and WSS) support (RFC 7118)...
A series of recently disclosed critical Bluetooth flaws that affect billions of Android, iOS, Windows and Linux devices have now been discovered in millions of...
The tool itself is impressive enough, serving as the backbone of the CIA’s malware processes, but there’s more. What’s interesting about the first leak in the...
The Trump Organization dismissed the domain names were ever Hacked. But a review of internet credentials by the AP and cybersecurity specialists shows...
Linux ELF x32 and x64 ASLR bypass exploit with stack-spraying. Properties: ASLR bypass Cross-platform Minimalistic Simplicity Unpatchable Dependencies: Linux 2...
The cryptocurrency hit an all-time high of $6,147.07 just a time after forcing through the $6,000 mark, according to data from application website CoinDesk...